This library aims at providing idiomatic nmap bindings for go developers, in order to make it easier to write security audit tools using golang.
Nmap (Network Mapper) is a free and open-source network scanner created by Gordon Lyon. Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses.
Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection. These features are extensible by scripts that provide more advanced service detection, vulnerability detection, and other features. Nmap can adapt to network conditions including latency and congestion during a scan.
Most pentest tools are currently written using Python and not Go, because it is easy to quickly write scripts, lots of libraries are available, and it's a simple language to use. However, for writing robust and reliable applications, Go is the better tool. It is statically compiled, has a static type system, much better performance, it is also a very simple language to use and goroutines are awesome... But I might be slighly biased, so feel free to disagree.
- All of
nmap's native options. - Additional idiomatic go filters for filtering hosts and ports.
- Helpful enums for nmap commands. (time templates, os families, port states, etc.)
- Complete documentation of each option, mostly insipred from nmap's documentation.
- Run a nmap scan asynchronously.
- Scan progress can be piped through a channel.
- Write the nmap output to a given file while also parsing it to the struct.
- Stream the nmap output to an
io.Writerinterface while also parsing it to the struct. - Functionality to show local interfaces and routes.
package main
import (
"context"
"fmt"
"log"
"time"
"github.com/Ullaakut/nmap/v3"
)
func main() {
ctx, cancel := context.WithTimeout(context.Background(), 5*time.Minute)
defer cancel()
// Equivalent to `/usr/local/bin/nmap -p 80,443,843 google.com facebook.com youtube.com`,
// with a 5-minute timeout.
scanner, err := nmap.NewScanner(
ctx,
nmap.WithTargets("google.com", "facebook.com", "youtube.com"),
nmap.WithPorts("80,443,843"),
)
if err != nil {
log.Fatalf("unable to create nmap scanner: %v", err)
}
result, warnings, err := scanner.Run()
if len(*warnings) > 0 {
log.Printf("run finished with warnings: %s\n", *warnings) // Warnings are non-critical errors from nmap.
}
if err != nil {
log.Fatalf("unable to run nmap scan: %v", err)
}
// Use the results to print an example output
for _, host := range result.Hosts {
if len(host.Ports) == 0 || len(host.Addresses) == 0 {
continue
}
fmt.Printf("Host %q:\n", host.Addresses[0])
for _, port := range host.Ports {
fmt.Printf("\tPort %d/%s %s %s\n", port.ID, port.Protocol, port.State, port.Service.Name)
}
}
fmt.Printf("Nmap done: %d hosts up scanned in %.2f seconds\n", len(result.Hosts), result.Stats.Finished.Elapsed)
}The program above outputs:
Host "172.217.16.46":
Port 80/tcp open http
Port 443/tcp open https
Port 843/tcp filtered unknown
Host "31.13.81.36":
Port 80/tcp open http
Port 443/tcp open https
Port 843/tcp open unknown
Host "216.58.215.110":
Port 80/tcp open http
Port 443/tcp open https
Port 843/tcp filtered unknown
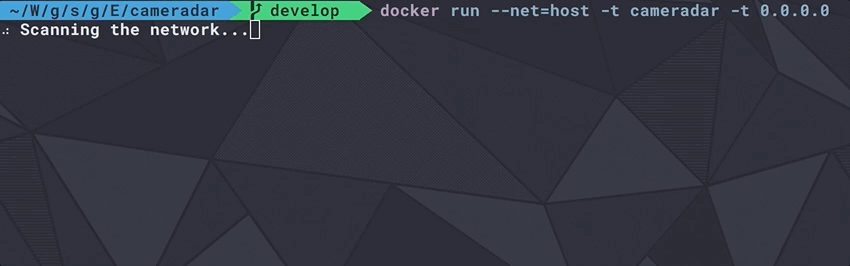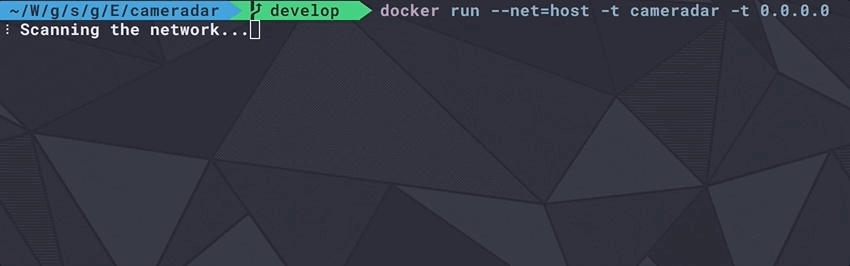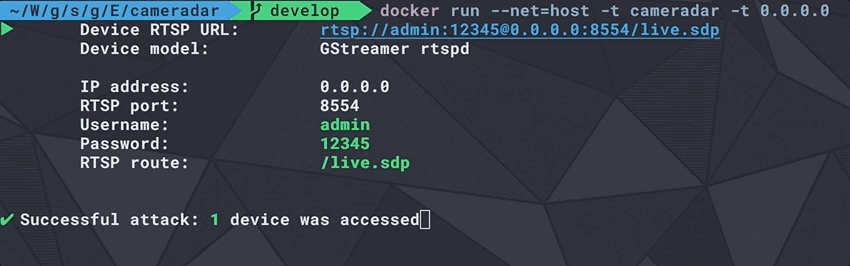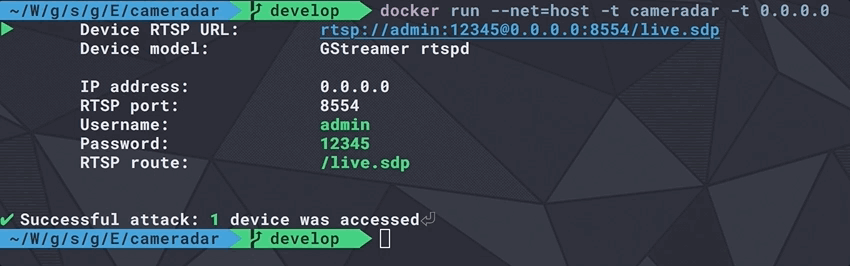
Nmap done: 3 hosts up scanned in 1.29 secondsCameradar already uses this library at its core to communicate with nmap, discover RTSP streams and access them remotely.
More examples: