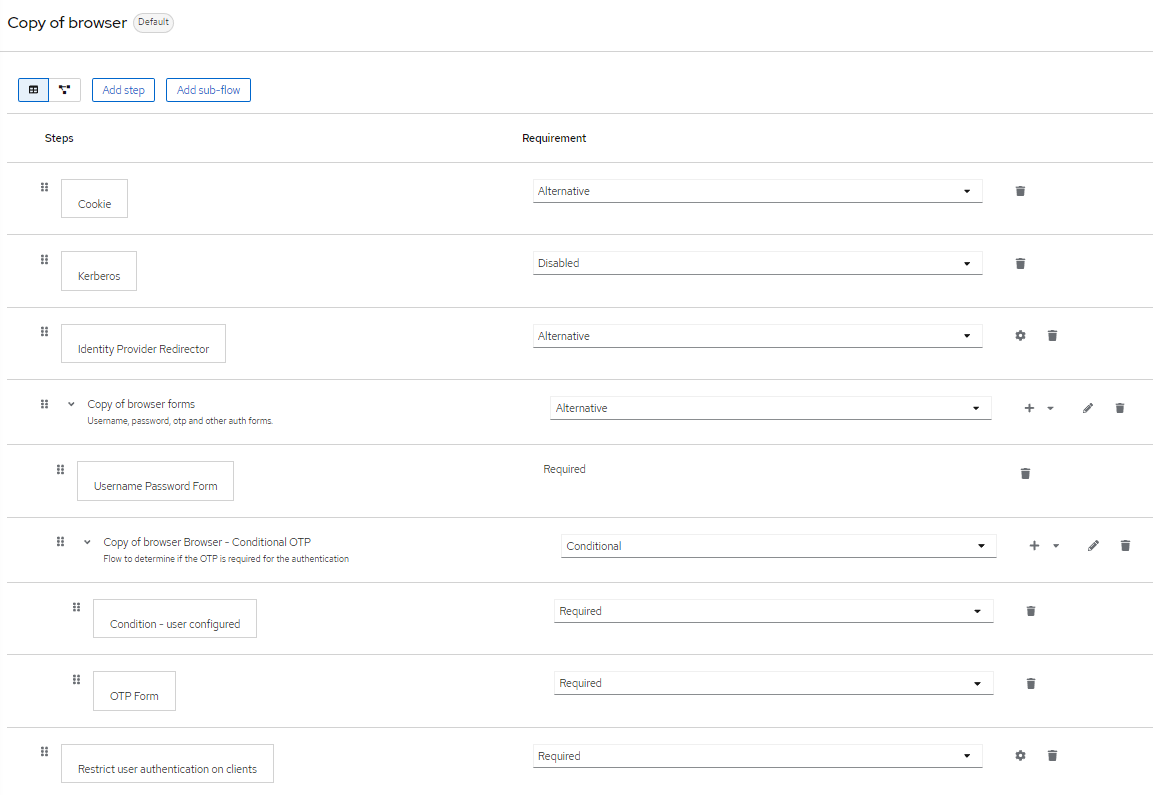
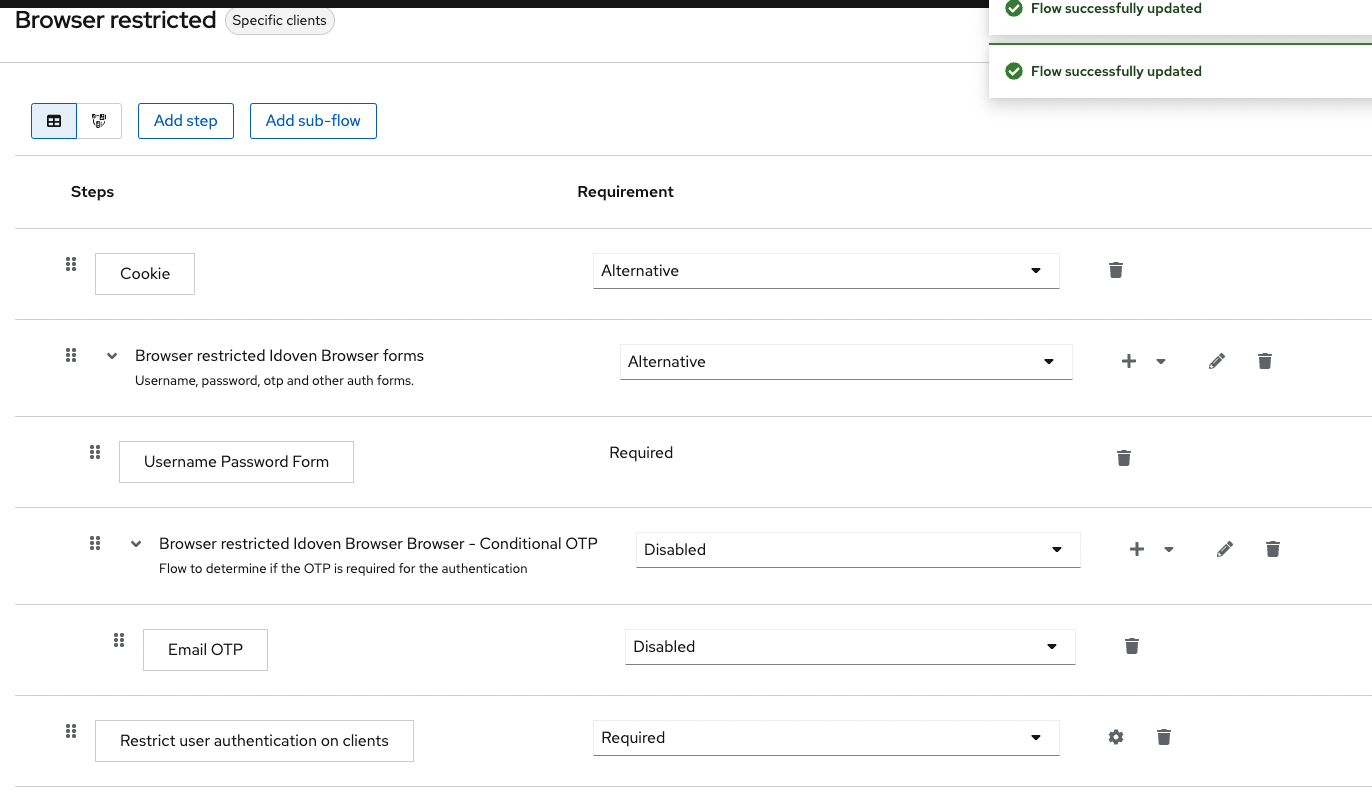
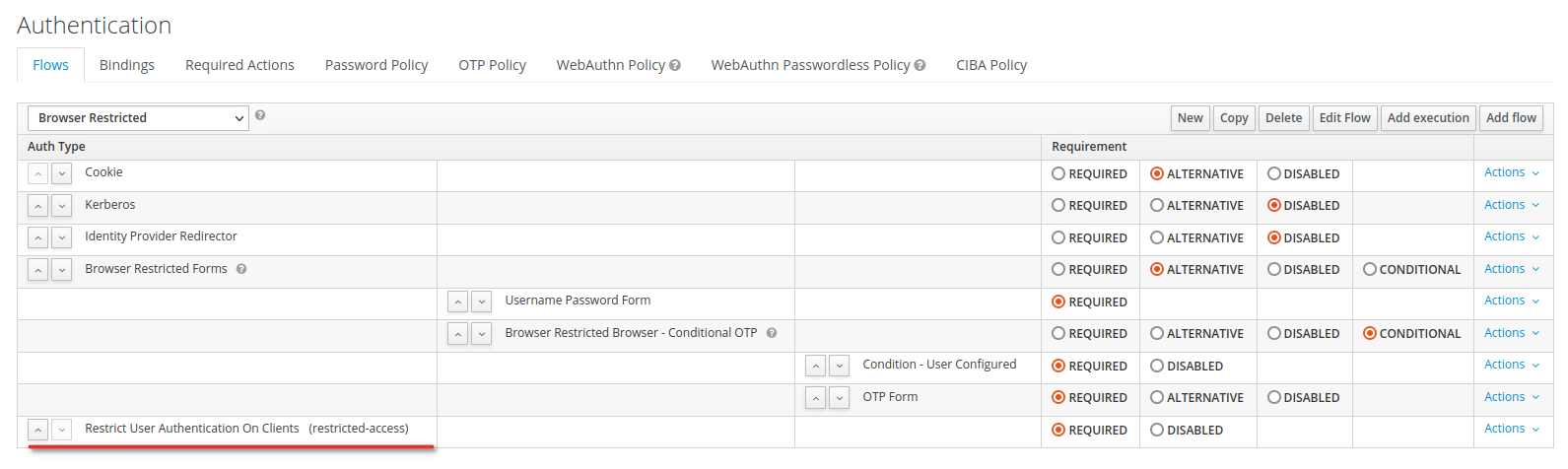
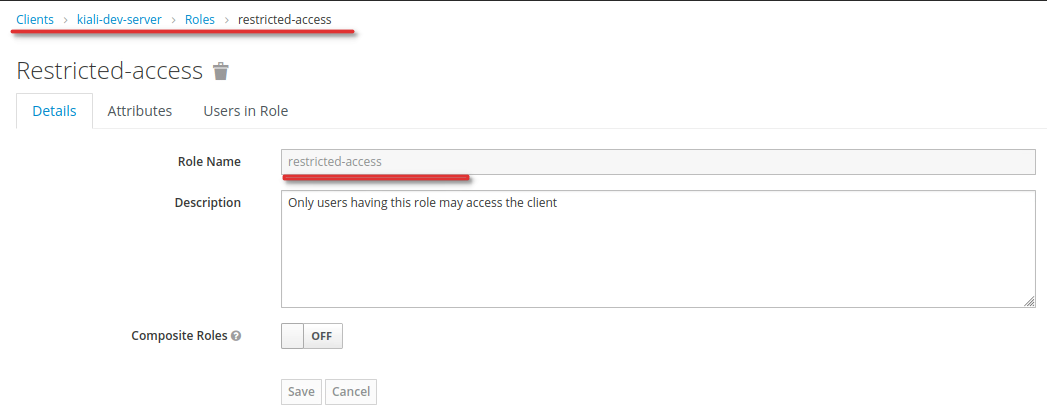
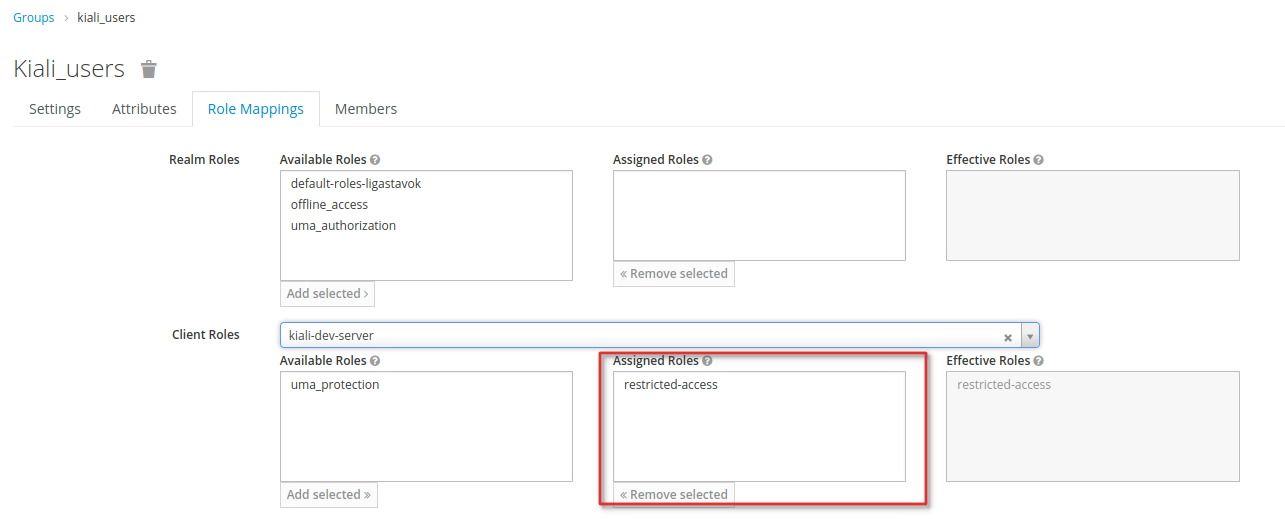
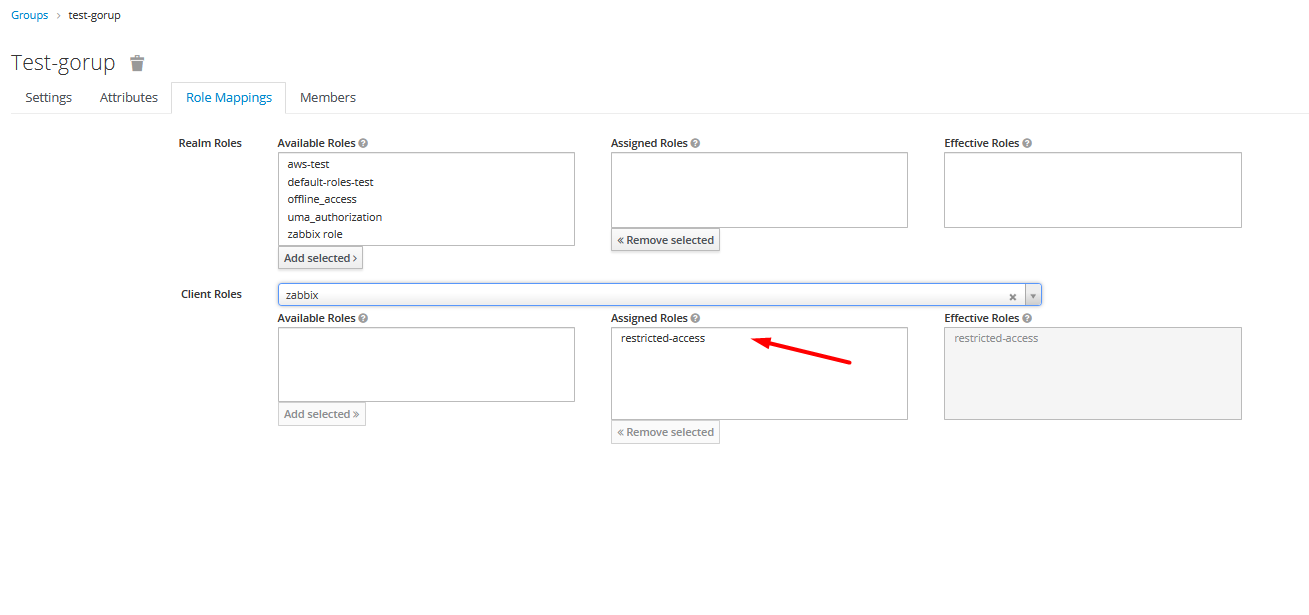
When the authenticator has not been configured (e.g. access provider is left empty or no authenticator config is present), RestrictClientAuthAuthenticator throws a NullPointerException:
{
"refId": 1,
"exceptionType": "java.lang.NullPointerException",
"message": null,
"frames": [
{
"class": "de.sventorben.keycloak.authorization.client.RestrictClientAuthAuthenticator",
"method": "getAccessProvider",
"line": 66
},
{
"class": "de.sventorben.keycloak.authorization.client.RestrictClientAuthAuthenticator",
"method": "authenticate",
"line": 34
},
{
"class": "org.keycloak.authentication.DefaultAuthenticationFlow",
"method": "processSingleFlowExecutionModel",
"line": 446
},
{
"class": "org.keycloak.authentication.DefaultAuthenticationFlow",
"method": "processFlow",
"line": 253
},
{
"class": "org.keycloak.authentication.DefaultAuthenticationFlow",
"method": "processSingleFlowExecutionModel",
"line": 389
},
{
"class": "org.keycloak.authentication.DefaultAuthenticationFlow",
"method": "processFlow",
"line": 253
},
{
"class": "org.keycloak.authentication.DefaultAuthenticationFlow",
"method": "continueAuthenticationAfterSuccessfulAction",
"line": 184
},
{
"class": "org.keycloak.authentication.DefaultAuthenticationFlow",
"method": "processAction",
"line": 164
},
{
"class": "org.keycloak.authentication.AuthenticationProcessor",
"method": "authenticationAction",
"line": 950
},
{
"class": "org.keycloak.services.resources.LoginActionsService",
"method": "processFlow",
"line": 312
},
{
"class": "org.keycloak.services.resources.LoginActionsService",
"method": "processAuthentication",
"line": 283
},
{
"class": "org.keycloak.services.resources.LoginActionsService",
"method": "authenticate",
"line": 267
},
{
"class": "org.keycloak.services.resources.LoginActionsService",
"method": "authenticateForm",
"line": 340
},
{
"class": "jdk.internal.reflect.NativeMethodAccessorImpl",
"method": "invoke0"
},
{
"class": "jdk.internal.reflect.NativeMethodAccessorImpl",
"method": "invoke",
"line": 62
},
{
"class": "jdk.internal.reflect.DelegatingMethodAccessorImpl",
"method": "invoke",
"line": 43
},
{
"class": "java.lang.reflect.Method",
"method": "invoke",
"line": 566
},
{
"class": "org.jboss.resteasy.core.MethodInjectorImpl",
"method": "invoke",
"line": 138
},
{
"class": "org.jboss.resteasy.core.ResourceMethodInvoker",
"method": "internalInvokeOnTarget",
"line": 546
},
{
"class": "org.jboss.resteasy.core.ResourceMethodInvoker",
"method": "invokeOnTargetAfterFilter",
"line": 435
},
{
"class": "org.jboss.resteasy.core.ResourceMethodInvoker",
"method": "lambda$invokeOnTarget$0",
"line": 396
},
{
"class": "org.jboss.resteasy.core.interception.PreMatchContainerRequestContext",
"method": "filter",
"line": 358
},
{
"class": "org.jboss.resteasy.core.ResourceMethodInvoker",
"method": "invokeOnTarget",
"line": 398
},
{
"class": "org.jboss.resteasy.core.ResourceMethodInvoker",
"method": "invoke",
"line": 365
},
{
"class": "org.jboss.resteasy.core.ResourceLocatorInvoker",
"method": "invokeOnTargetObject",
"line": 150
},
{
"class": "org.jboss.resteasy.core.ResourceLocatorInvoker",
"method": "invoke",
"line": 104
},
{
"class": "org.jboss.resteasy.core.SynchronousDispatcher",
"method": "invoke",
"line": 440
},
{
"class": "org.jboss.resteasy.core.SynchronousDispatcher",
"method": "lambda$invoke$4",
"line": 229
},
{
"class": "org.jboss.resteasy.core.SynchronousDispatcher",
"method": "lambda$preprocess$0",
"line": 135
},
{
"class": "org.jboss.resteasy.core.interception.PreMatchContainerRequestContext",
"method": "filter",
"line": 358
},
{
"class": "org.jboss.resteasy.core.SynchronousDispatcher",
"method": "preprocess",
"line": 138
},
{
"class": "org.jboss.resteasy.core.SynchronousDispatcher",
"method": "invoke",
"line": 215
},
{
"class": "org.jboss.resteasy.plugins.server.servlet.ServletContainerDispatcher",
"method": "service",
"line": 245
},
{
"class": "org.jboss.resteasy.plugins.server.servlet.HttpServletDispatcher",
"method": "service",
"line": 61
},
{
"class": "org.jboss.resteasy.plugins.server.servlet.HttpServletDispatcher",
"method": "service",
"line": 56
},
{
"class": "javax.servlet.http.HttpServlet",
"method": "service",
"line": 590
},
{
"class": "io.undertow.servlet.handlers.ServletHandler",
"method": "handleRequest",
"line": 74
},
{
"class": "io.undertow.servlet.handlers.FilterHandler$FilterChainImpl",
"method": "doFilter",
"line": 129
},
{
"class": "org.keycloak.provider.wildfly.WildFlyRequestFilter",
"method": "lambda$doFilter$0",
"line": 41
},
{
"class": "org.keycloak.services.filters.AbstractRequestFilter",
"method": "filter",
"line": 43
},
{
"class": "org.keycloak.provider.wildfly.WildFlyRequestFilter",
"method": "doFilter",
"line": 39
},
{
"class": "io.undertow.servlet.core.ManagedFilter",
"method": "doFilter",
"line": 61
},
{
"class": "io.undertow.servlet.handlers.FilterHandler$FilterChainImpl",
"method": "doFilter",
"line": 131
},
{
"class": "io.undertow.servlet.handlers.FilterHandler",
"method": "handleRequest",
"line": 84
},
{
"class": "io.undertow.servlet.handlers.security.ServletSecurityRoleHandler",
"method": "handleRequest",
"line": 62
},
{
"class": "io.undertow.servlet.handlers.ServletChain$1",
"method": "handleRequest",
"line": 68
},
{
"class": "io.undertow.servlet.handlers.ServletDispatchingHandler",
"method": "handleRequest",
"line": 36
},
{
"class": "org.wildfly.extension.undertow.security.SecurityContextAssociationHandler",
"method": "handleRequest",
"line": 78
},
{
"class": "io.undertow.server.handlers.PredicateHandler",
"method": "handleRequest",
"line": 43
},
{
"class": "io.undertow.servlet.handlers.RedirectDirHandler",
"method": "handleRequest",
"line": 68
},
{
"class": "io.undertow.servlet.handlers.security.SSLInformationAssociationHandler",
"method": "handleRequest",
"line": 117
},
{
"class": "io.undertow.servlet.handlers.security.ServletAuthenticationCallHandler",
"method": "handleRequest",
"line": 57
},
{
"class": "io.undertow.server.handlers.PredicateHandler",
"method": "handleRequest",
"line": 43
},
{
"class": "io.undertow.security.handlers.AbstractConfidentialityHandler",
"method": "handleRequest",
"line": 46
},
{
"class": "io.undertow.servlet.handlers.security.ServletConfidentialityConstraintHandler",
"method": "handleRequest",
"line": 64
},
{
"class": "io.undertow.security.handlers.AuthenticationMechanismsHandler",
"method": "handleRequest",
"line": 60
},
{
"class": "io.undertow.servlet.handlers.security.CachedAuthenticatedSessionHandler",
"method": "handleRequest",
"line": 77
},
{
"class": "io.undertow.security.handlers.NotificationReceiverHandler",
"method": "handleRequest",
"line": 50
},
{
"class": "io.undertow.security.handlers.AbstractSecurityContextAssociationHandler",
"method": "handleRequest",
"line": 43
},
{
"class": "io.undertow.server.handlers.PredicateHandler",
"method": "handleRequest",
"line": 43
},
{
"class": "org.wildfly.extension.undertow.security.jacc.JACCContextIdHandler",
"method": "handleRequest",
"line": 61
},
{
"class": "io.undertow.server.handlers.PredicateHandler",
"method": "handleRequest",
"line": 43
},
{
"class": "org.wildfly.extension.undertow.deployment.GlobalRequestControllerHandler",
"method": "handleRequest",
"line": 68
},
{
"class": "io.undertow.servlet.handlers.SendErrorPageHandler",
"method": "handleRequest",
"line": 52
},
{
"class": "io.undertow.server.handlers.PredicateHandler",
"method": "handleRequest",
"line": 43
},
{
"class": "io.undertow.servlet.handlers.ServletInitialHandler",
"method": "handleFirstRequest",
"line": 269
},
{
"class": "io.undertow.servlet.handlers.ServletInitialHandler",
"method": "access$100",
"line": 78
},
{
"class": "io.undertow.servlet.handlers.ServletInitialHandler$2",
"method": "call",
"line": 133
},
{
"class": "io.undertow.servlet.handlers.ServletInitialHandler$2",
"method": "call",
"line": 130
},
{
"class": "io.undertow.servlet.core.ServletRequestContextThreadSetupAction$1",
"method": "call",
"line": 48
},
{
"class": "io.undertow.servlet.core.ContextClassLoaderSetupAction$1",
"method": "call",
"line": 43
},
{
"class": "org.wildfly.extension.undertow.security.SecurityContextThreadSetupAction",
"method": "lambda$create$0",
"line": 105
},
{
"class": "org.wildfly.extension.undertow.deployment.UndertowDeploymentInfoService$UndertowThreadSetupAction",
"method": "lambda$create$0",
"line": 1530
},
{
"class": "org.wildfly.extension.undertow.deployment.UndertowDeploymentInfoService$UndertowThreadSetupAction",
"method": "lambda$create$0",
"line": 1530
},
{
"class": "org.wildfly.extension.undertow.deployment.UndertowDeploymentInfoService$UndertowThreadSetupAction",
"method": "lambda$create$0",
"line": 1530
},
{
"class": "org.wildfly.extension.undertow.deployment.UndertowDeploymentInfoService$UndertowThreadSetupAction",
"method": "lambda$create$0",
"line": 1530
},
{
"class": "io.undertow.servlet.handlers.ServletInitialHandler",
"method": "dispatchRequest",
"line": 249
},
{
"class": "io.undertow.servlet.handlers.ServletInitialHandler",
"method": "access$000",
"line": 78
},
{
"class": "io.undertow.servlet.handlers.ServletInitialHandler$1",
"method": "handleRequest",
"line": 99
},
{
"class": "io.undertow.server.Connectors",
"method": "executeRootHandler",
"line": 387
},
{
"class": "io.undertow.server.HttpServerExchange$1",
"method": "run",
"line": 841
},
{
"class": "org.jboss.threads.ContextClassLoaderSavingRunnable",
"method": "run",
"line": 35
},
{
"class": "org.jboss.threads.EnhancedQueueExecutor",
"method": "safeRun",
"line": 1990
},
{
"class": "org.jboss.threads.EnhancedQueueExecutor$ThreadBody",
"method": "doRunTask",
"line": 1486
},
{
"class": "org.jboss.threads.EnhancedQueueExecutor$ThreadBody",
"method": "run",
"line": 1377
},
{
"class": "org.xnio.XnioWorker$WorkerThreadFactory$1$1",
"method": "run",
"line": 1280
},
{
"class": "java.lang.Thread",
"method": "run",
"line": 829
}
]
}Should not throw a NullPointerException but use the default authenticator and access provider client-role instead.