This repository contains the source code for Semgrep OSS (open-source software). Semgrep OSS is a fast, open-source, static analysis tool for searching code, finding bugs, and enforcing code standards at editor, commit, and CI time. Semgrep is a semantic grep for code: where grep "2" would only match the exact string 2, Semgrep would match x = 1; y = x + 1 when searching for 2. And it does this in 30+ languages! Semgrep rules look like the code you already write; no abstract syntax trees, regex wrestling, or painful DSLs: read more below.
For companies who need SAST, SCA, and Secret scanning, we provide a product suite on top of Semgrep OSS that scans code and package dependencies for known issues, software vulnerabilities, and finds secrets with high accuracy:
- Semgrep Code to find bugs & vulnerabilities using the deeper, interfile-analysis enabled Pro engine and high-accuracy Pro rules in addition to the community rules
- Semgrep Supply Chain to find dependencies with known vulnerabilities function-level reachability analysis
- Semgrep Secrets to find hard-coded credentials that shouldn't be checked into source code
Semgrep analyzes code locally on your computer or in your build environment: by default, code is never uploaded. Get started →.
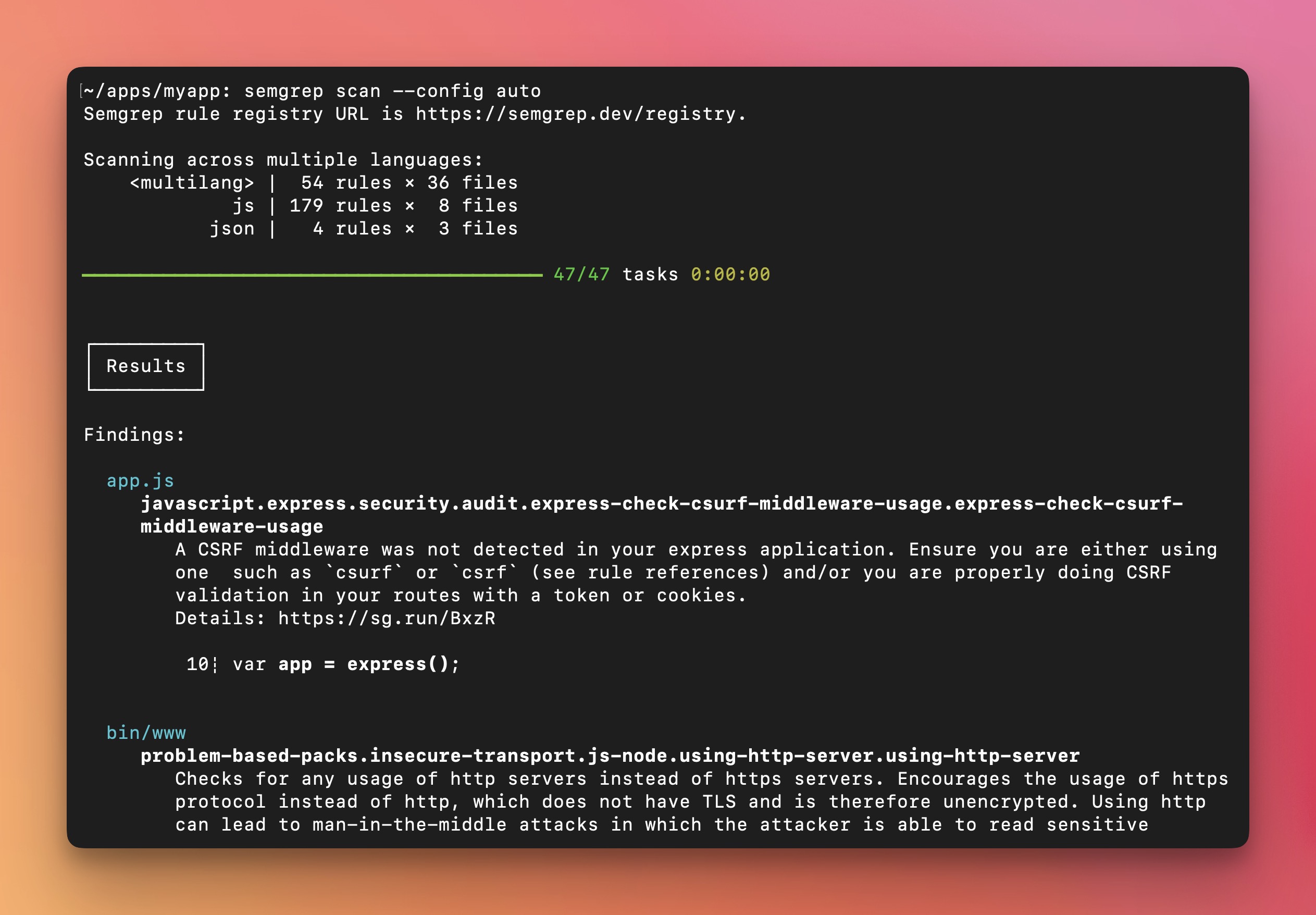
Semgrep Code supports 30+ languages, including:
Apex · Bash · C · C++ · C# · Clojure · Dart · Dockerfile · Elixir · HTML · Go · Java · JavaScript · JSX · JSON · Julia · Jsonnet · Kotlin · Lisp · Lua · OCaml · PHP · Python · R · Ruby · Rust · Scala · Scheme · Solidity · Swift · Terraform · TypeScript · TSX · YAML · XML · Generic (ERB, Jinja, etc.)
Semgrep Supply Chain supports 12 languages across 15 package managers, including:
C# (NuGet) · Dart (Pub) · Go (Go modules, go mod) · Java (Gradle, Maven) · Javascript/Typescript (npm, Yarn, Yarn 2, Yarn 3, pnpm) · Kotlin (Gradle, Maven) · PHP (Composer) · Python (pip, pip-tool, Pipenv, Poetry) · Ruby (RubyGems) · Rust (Cargo) · Scala (Maven) · Swift (SwiftPM)
For more information, see Supported languages.
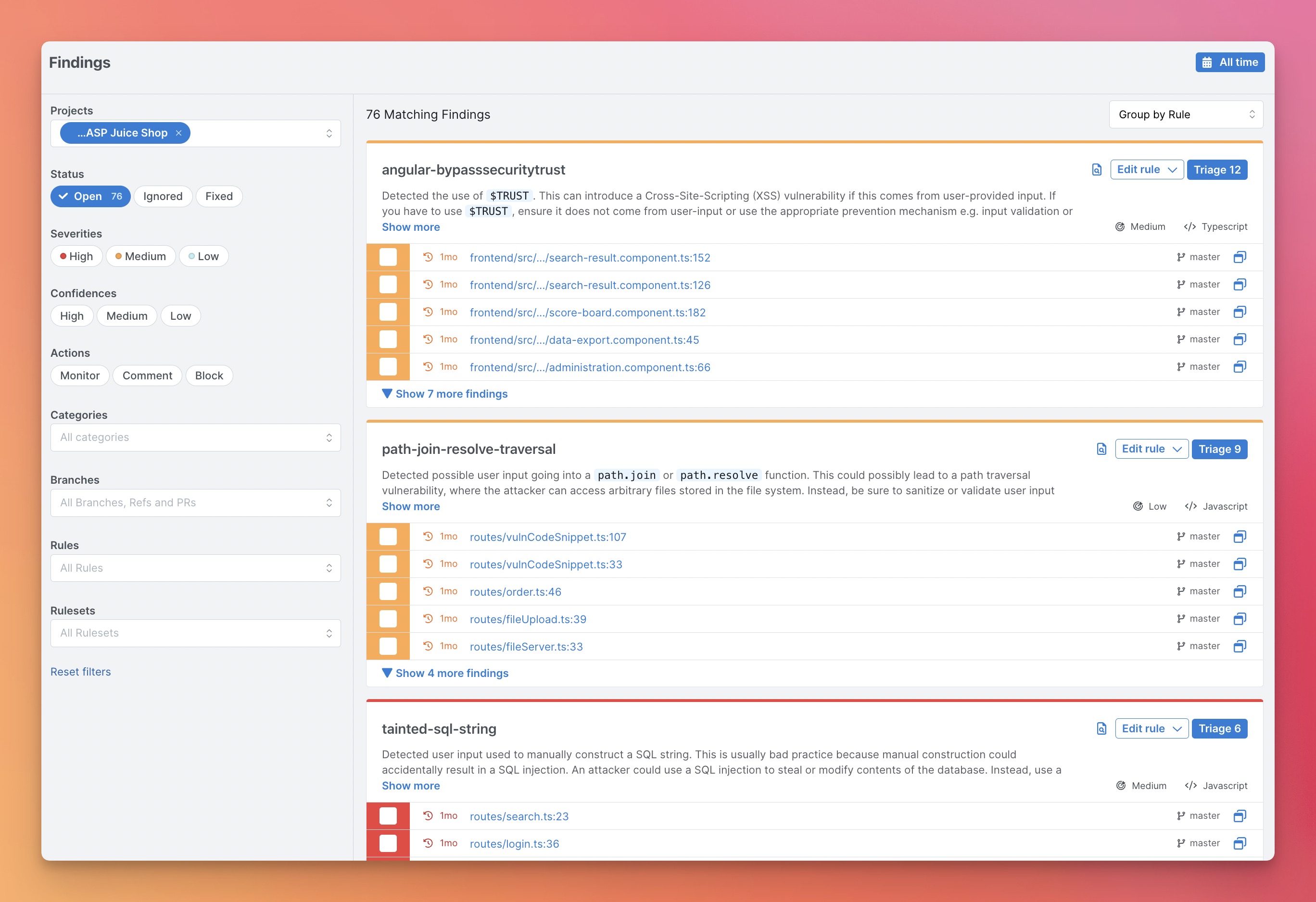
For new users, we recommend starting with the Semgrep AppSec Platform because it provides a visual interface, a demo project, result triaging and exploration workflows, and makes setup in CI/CD fast. Scans are still local and code isn't uploaded. Alternatively, you can also start with the CLI and navigate the terminal output to run one-off searches.
-
Register on semgrep.dev
-
Explore the demo findings to learn how Semgrep works
-
Scan your project by navigating to
Projects > Scan New Project > Run scan in CI -
Select your version control system and follow the onboarding steps to add your project. After this setup, Semgrep will scan your project after every pull request.
-
[Optional] If you want to run Semgrep locally, follow the steps in the CLI section.
If there are any issues, please ask for help in the Semgrep Slack.
- Install Semgrep CLI
# For macOS
$ brew install semgrep
# For Ubuntu/WSL/Linux/macOS
$ python3 -m pip install semgrep
# To try Semgrep without installation run via Docker
$ docker run -it -v "${PWD}:/src" semgrep/semgrep semgrep login
$ docker run -e SEMGREP_APP_TOKEN=<TOKEN> --rm -v "${PWD}:/src" semgrep/semgrep semgrep ci
- Run
semgrep loginto create your account and login to Semgrep.
Logging into Semgrep gets you access to:
- Semgrep Supply Chain: A dependency scanner that detects reachable vulnerabilities in third party libraries
- Semgrep Code's Pro rules: 600+ high confidence rules written by Semgrep's security research team
- Semgrep Code's Pro engine: An advanced code analysis engine, designed to detect complex vulnerabilities, and reduce false positives
-
Go to your app's root directory and run
semgrep ci. This will scan your project to check for vulnerabilities in your source code and its dependencies. -
Try writing your own query interactively with
-e. For example, a check for Python == where the left and right hand sides are the same (potentially a bug):$ semgrep -e '$X == $X' --lang=py path/to/src
The Semgrep ecosystem includes the following products:
- Semgrep Code - Scan your code with Semgrep's proprietary rules (written by our Security Research team) using our cross-file and cross-function analysis. Designed to find OWASP Top 10 vulnerabilities and protect against critical security risks. Semgrep Code is available on both free and paid tiers.
- Semgrep Supply Chain (SSC) - A high-signal dependency scanner that detects reachable vulnerabilities in open source third-party libraries and functions across the software development life cycle (SDLC). Semgrep Supply Chain is available on both free and paid tiers.
- Semgrep Secrets [NEW!] - Secrets detection that uses semantic analysis, improved entropy analysis, and validation together to accurately detect sensitive credentials in developer workflows. Book a demo to request early access to the product.
- Semgrep AppSec Platform - Deploy, manage, and monitor Semgrep at scale, with free and paid tiers. Integrates with continuous integration (CI) providers such as GitHub, GitLab, CircleCI, and more.
- Semgrep OSS Engine - The open-source engine and community-contributed rules at the heart of everything (this project).
To learn more about Semgrep, visit:
- Semgrep Playground - An online interactive tool for writing and sharing rules.
- Semgrep Registry - 2,000+ community-driven rules covering security, correctness, and dependency vulnerabilities.
Join hundreds of thousands of other developers and security engineers already using Semgrep at companies like GitLab, Dropbox, Slack, Figma, Shopify, HashiCorp, Snowflake, and Trail of Bits.
Semgrep is developed and commercially supported by Semgrep, Inc., a software security company.
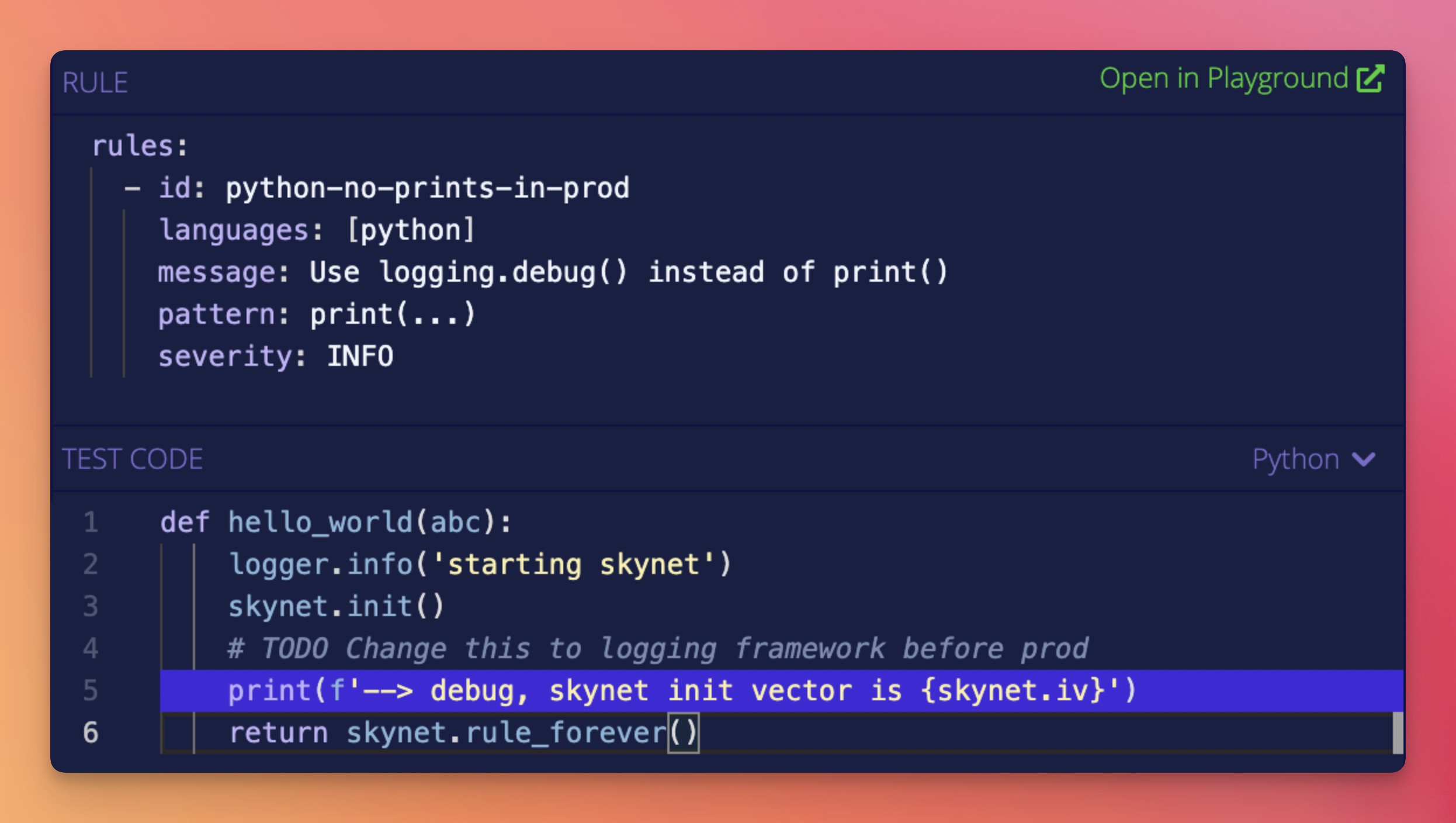
Semgrep rules look like the code you already write; no abstract syntax trees, regex wrestling, or painful DSLs. Here's a quick rule for finding Python print() statements.
Run it online in Semgrep’s Playground by clicking here.
Visit Docs > Rule examples for use cases and ideas.
| Use case | Semgrep rule |
|---|---|
| Ban dangerous APIs | Prevent use of exec |
| Search routes and authentication | Extract Spring routes |
| Enforce the use secure defaults | Securely set Flask cookies |
| Tainted data flowing into sinks | ExpressJS dataflow into sandbox.run |
| Enforce project best-practices | Use assertEqual for == checks, Always check subprocess calls |
| Codify project-specific knowledge | Verify transactions before making them |
| Audit security hotspots | Finding XSS in Apache Airflow, Hardcoded credentials |
| Audit configuration files | Find S3 ARN uses |
| Migrate from deprecated APIs | DES is deprecated, Deprecated Flask APIs, Deprecated Bokeh APIs |
| Apply automatic fixes | Use listenAndServeTLS |
Visit Docs > Extensions to learn about using Semgrep in your editor or pre-commit. When integrated into CI and configured to scan pull requests, Semgrep will only report issues introduced by that pull request; this lets you start using Semgrep without fixing or ignoring pre-existing issues!
Browse the full Semgrep documentation on the website. If you’re new to Semgrep, check out Docs > Getting started or the interactive tutorial.
Using remote configuration from the Registry (like --config=p/ci) reports pseudonymous rule metrics to semgrep.dev.
Using configs from local files (like --config=xyz.yml) does not enable metrics.
To disable Registry rule metrics, use --metrics=off.
The Semgrep privacy policy describes the principles that guide data-collection decisions and the breakdown of the data that are and are not collected when the metrics are enabled.
- Frequently asked questions (FAQs)
- Contributing
- Build instructions for developers
- Ask questions in the Semgrep community Slack
- CLI reference and exit codes
- Semgrep YouTube channel
- License (LGPL-2.1)
- Licensing Semgrep
To upgrade, run the command below associated with how you installed Semgrep:
# Using Homebrew
$ brew upgrade semgrep
# Using pip
$ python3 -m pip install --upgrade semgrep
# Using Docker
$ docker pull semgrep/semgrep:latest