TheFatRat is an exploiting tool which compiles a malware with famous payload, and then the compiled maware can be executed on Linux , Windows , Mac and Android. TheFatRat Provides An Easy way to create Backdoors and Payload which can bypass most anti-virus.
This tool is for educational purpose only, usage of TheFatRat for attacking targets without prior mutual consent is illegal. Developers assume no liability and are not responsible for any misuse or damage cause by this program.
- Fully Automating MSFvenom & Metasploit.
- Local or remote listener Generation.
- Easily Make Backdoor by category Operating System.
- Generate payloads in Various formats.
- Bypass anti-virus backdoors.
- File pumper that you can use for increasing the size of your files.
- The ability to detect external IP & Interface address .
- Automatically creates AutoRun files for USB / CDROM exploitation
- Yes, you're probably correct. Feel free to "Not use it" and there is a pull button to "Make it better".
Instructions on how to install TheFatRat
git clone https://github.com/Screetsec/TheFatRat.git
cd TheFatRat
chmod +x setup.sh && ./setup.shcd TheFatRat
./update && chmod +x setup.sh && ./setup.shchk_tools script to use in case of problems in setup.sh of fatrat this script will check if everything is in the right version to run fatrat and will also provide you a solution for the problem
cd TheFatRat
chmod +x chk_tools
./chk_tools
| Front View | Sample Feature |
|---|---|
 |
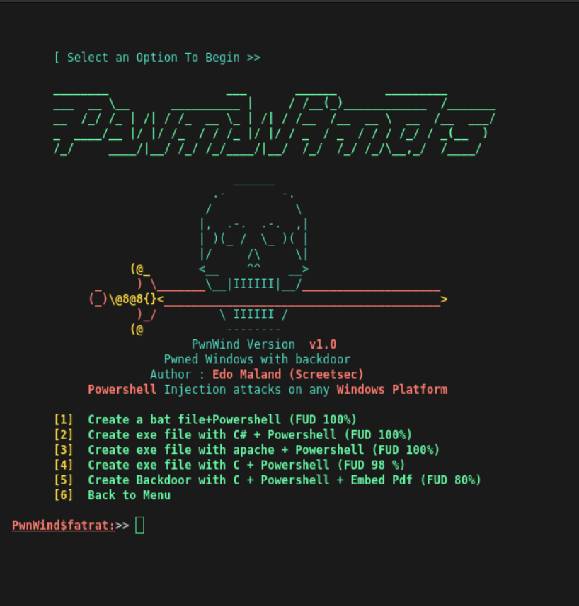 |
- Documentation Available in Modules CEH v9 and V10 , Download source here
- Published in International Journal of Cyber-Security and Digital Forensics
- Youtube Videos
- How To Download & Install TheFatRat
- TheFatRat 1.9.6 - Trodebi ( Embed Trojan into Debian Package )
- hacking windows 10 with TheFatRat
- Hacking Windows using TheFatRat + Apache2 Server + Ettercap + Metasploit
- Hacking with a Microsoft Office Word Document from TheFatRat
- XSS to powershell attack and bypass Antivirus using BeEF + TheFatRat + Metasploit
- TheFatRat - Hacking Over WAN - Embedding Payload in Original Android APK - Without Port Forwarding
- How To Automatically Embed Payloads In APK's - Evil-Droid, Thefatrat & Apkinjector
- Bind FUD Payload with JPG and Hack over WAN with TheFatRat
All notable changes to this project will be documented in this file.
- Read the document before making an issue
- Veil-Framework /Veil - Veil Framework
- Shellter - Shellter AV Evasion Artware
- Unicorn - Trustedsec
- MSFvenom Payload Creator (MSFPC) - g0tmi1k
- Venom - Pedro Ubuntu
- Phantom-Evasion - Diego Cornacchini
- Offensive Security - Offensive Security
- dracOs Linux - Penetration Testing OS From Indonesia
- peterpt - Maintainer & Contributor
- Dana James Traversie - backdoor_apk
- z0noxz - Powerstager
- TrustedSec - Unicorn
- Raphael Mudge - External Source
- astr0baby - Reference Source
- NgeSEC Community
- Gauli(dot)Net - Lab Penetration
TheFatRat is made with 🖤 by Edo Maland & All Contributors. See the License file for more details.

















