Pure Swagger
This is a tool that provides the Pure Storage FlashArray and FlashBlade API documentation into the popular interactive Swagger UI. This lets you browse the API documentation in a convenient format and even execute API calls interactively directly to a FlashArray or FlashBlade!
Try It:
Requires docker to be installed
docker run -it --rm -p 80:5000 quay.io/purestorage/swagger
Then open your browser to http://127.0.0.1 Then select an API spec and enter your FlashArray or FlashBlade IP.
To stop run:
just ctrl^c on the console docker container
Update to the latest version
docker pull quay.io/purestorage/swagger
Authentication Examples Videos
FlashBlade 1.x API Token
FlashArray 1.x API Token
FlashArray 2.2+ API Token
FlashArray 2.0+ OAuth2 API Client Auth
Screenshots
Documentation in collapsable easy to read format
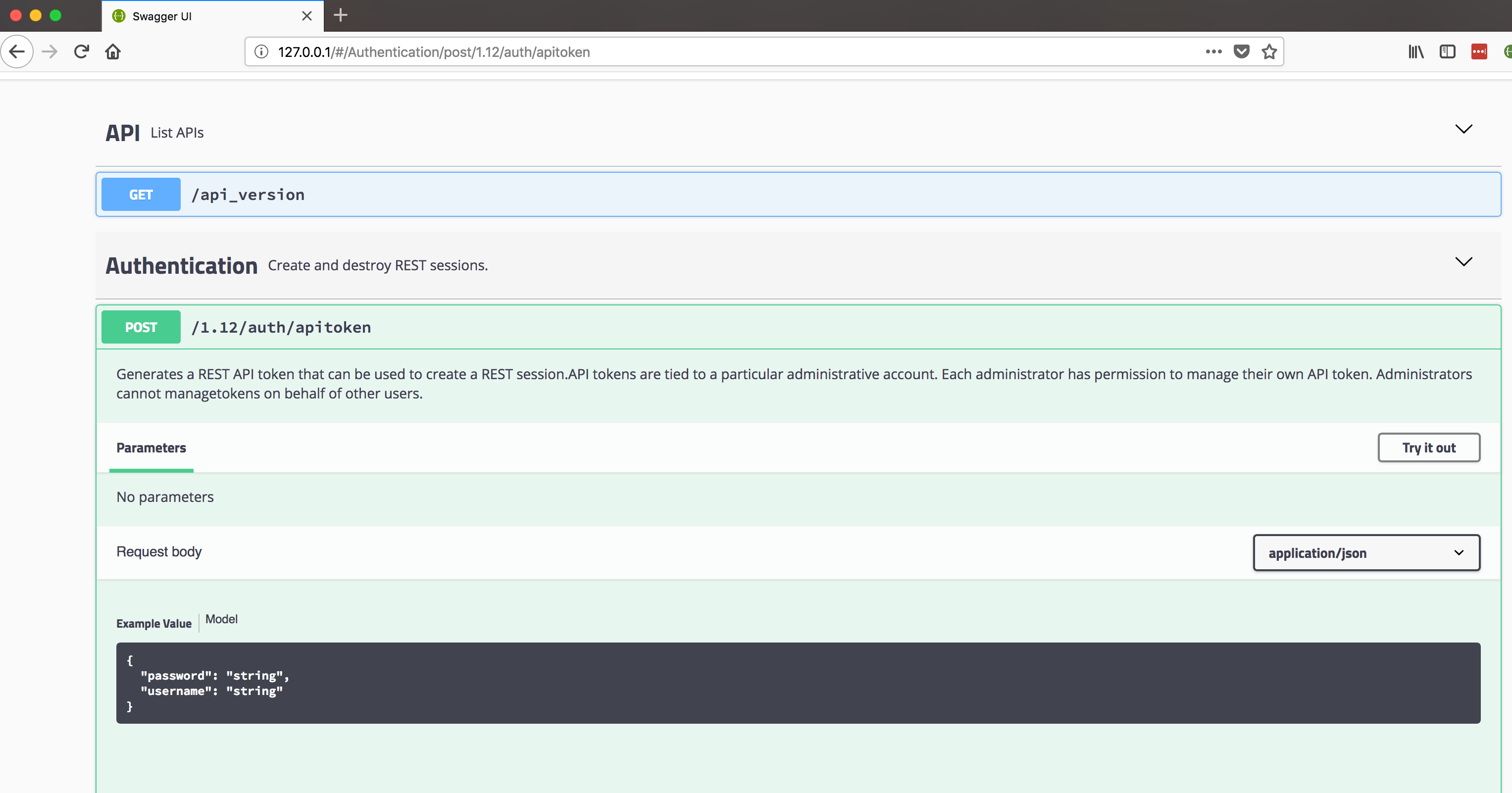
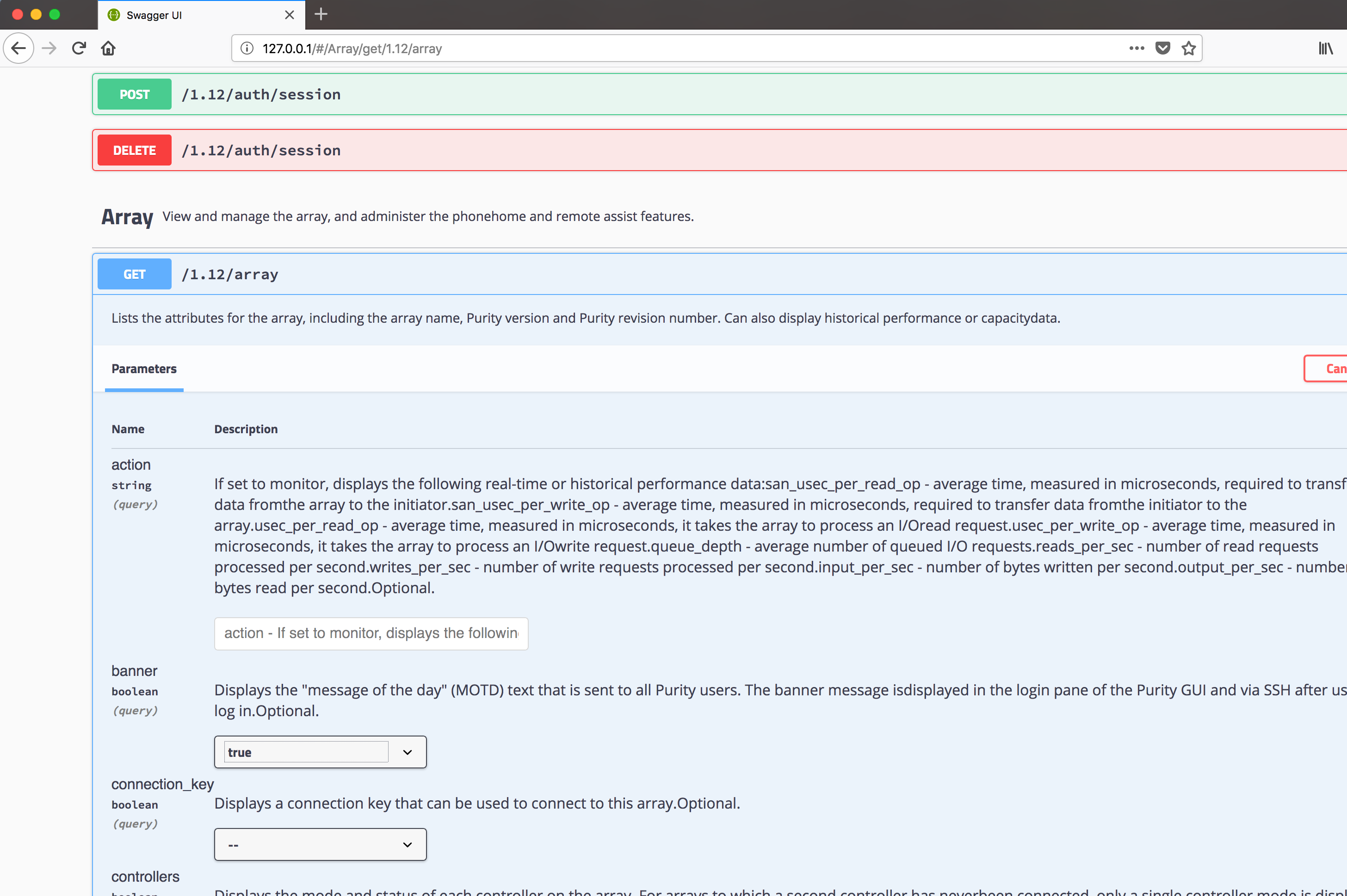
See detailed paramater information
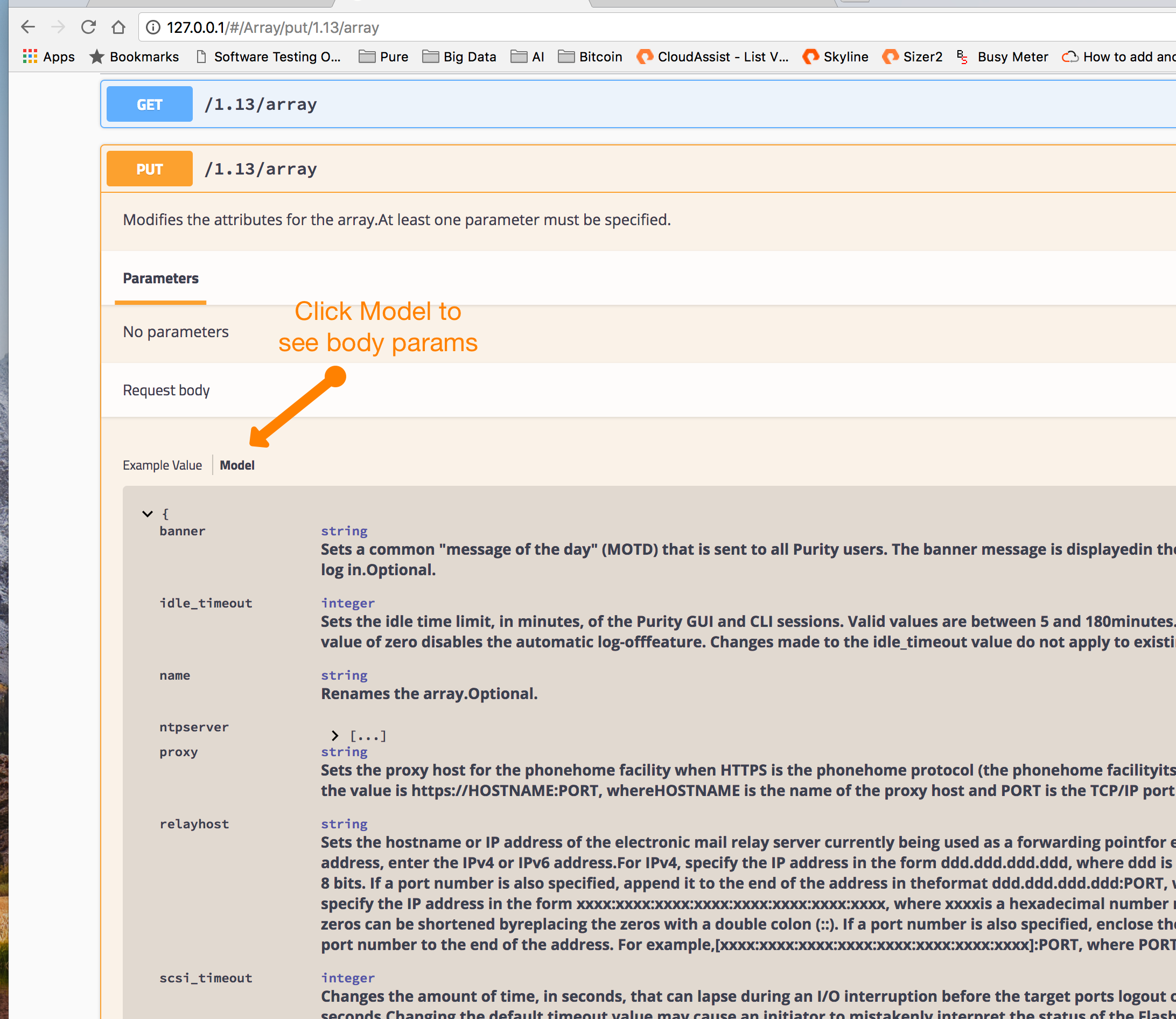
See body param documentation
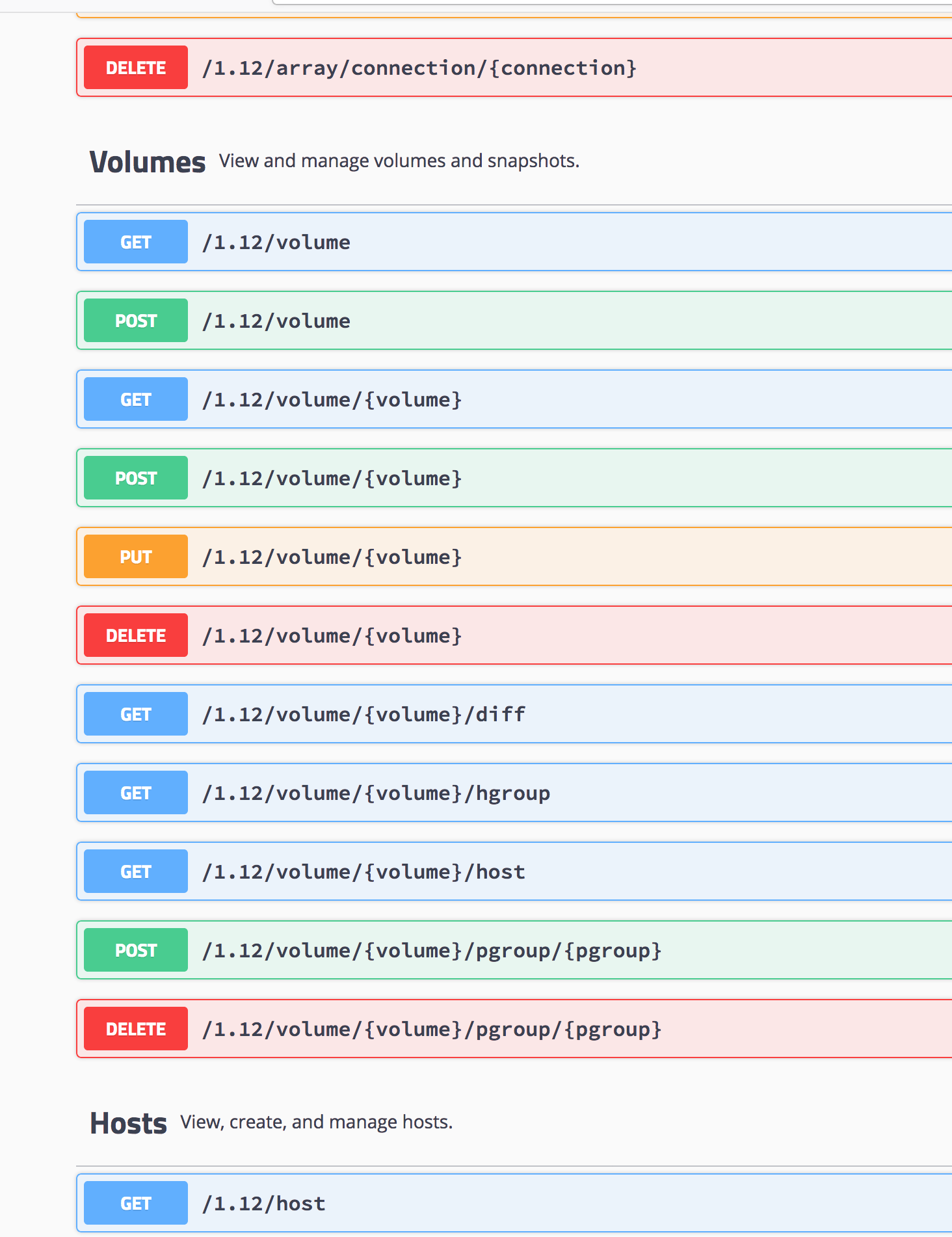
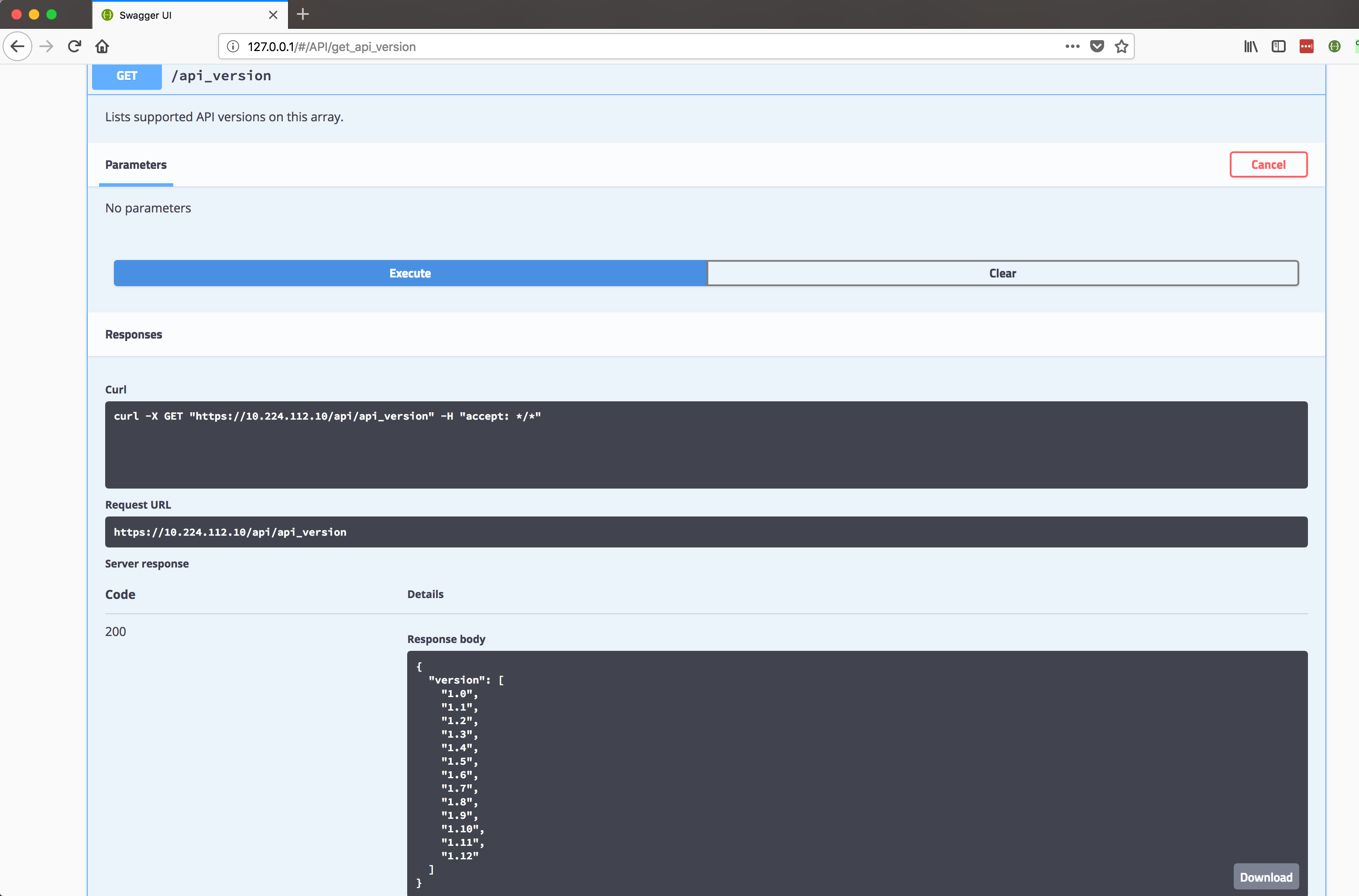
Every Endpoint is documented !
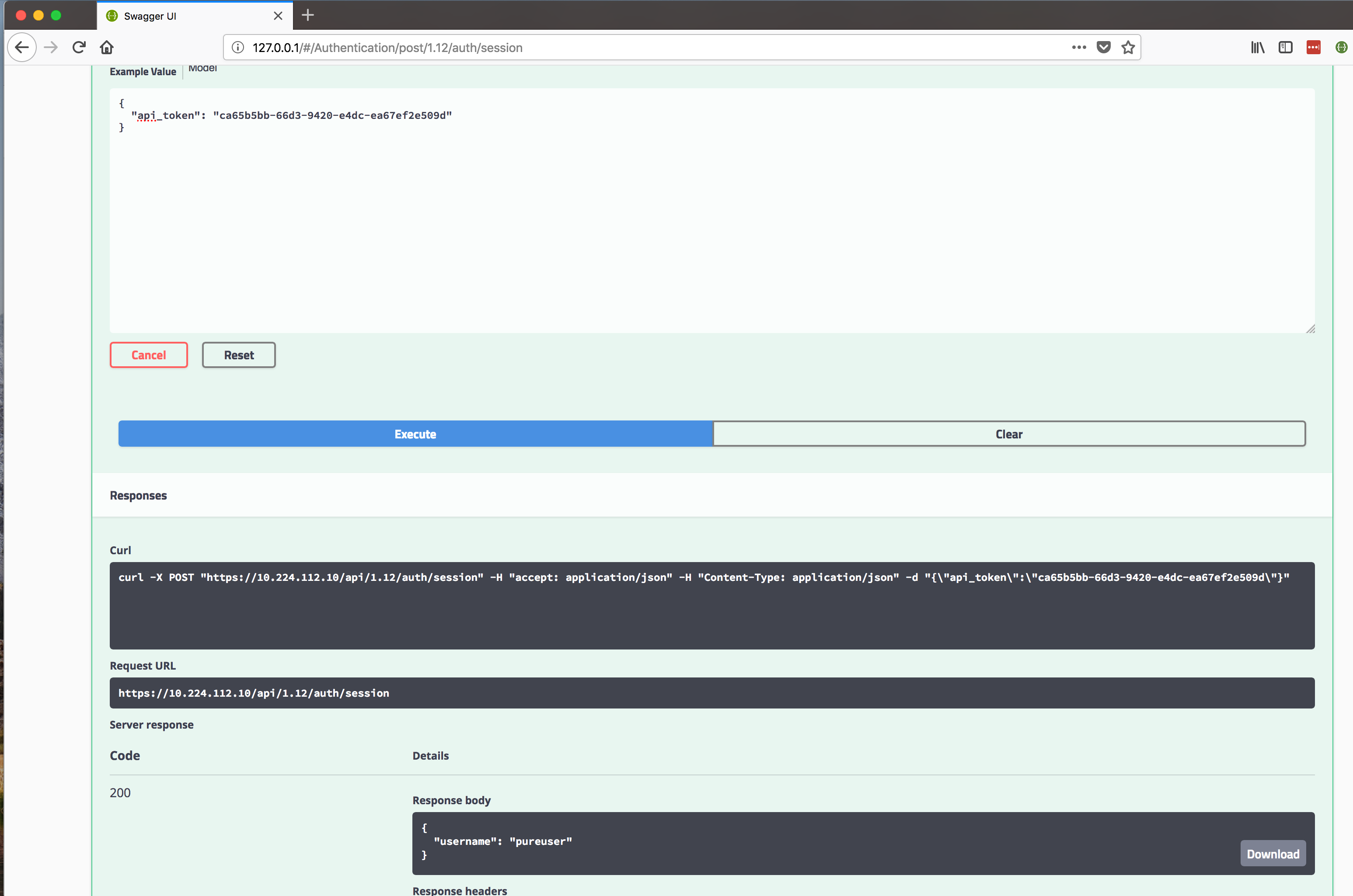
Actually send API commands to an Array:
Start a session:
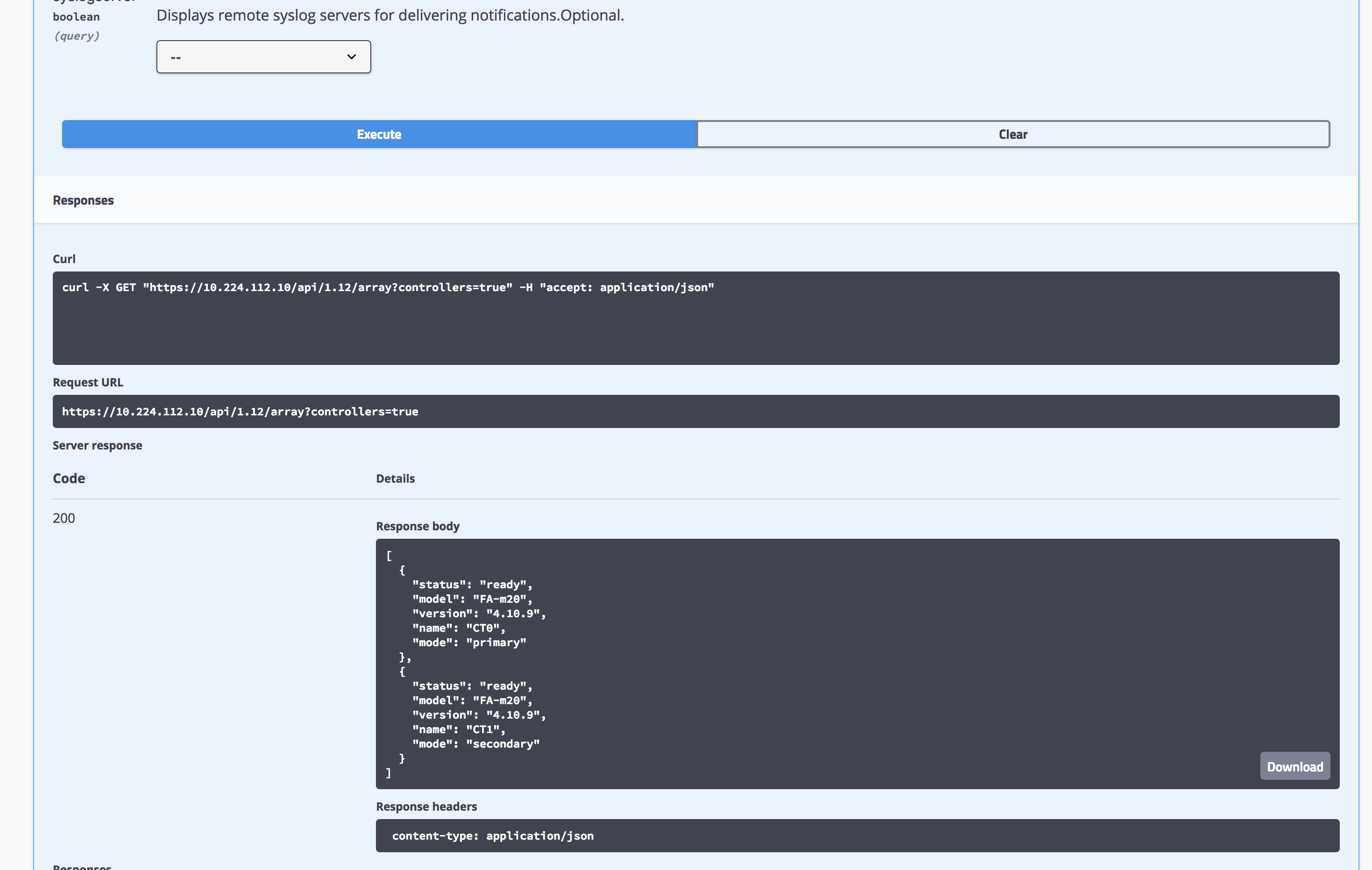
Get Controller Info:
Notes:
In order to send API calls to an array you must
- Have a FlashArray or FlashBlade and login credentials