Unlock Android devices by bruteforcing the lockscreen PIN.
Transform your Kali Nethunter phone into a PIN cracking powerhouse for Android devices!
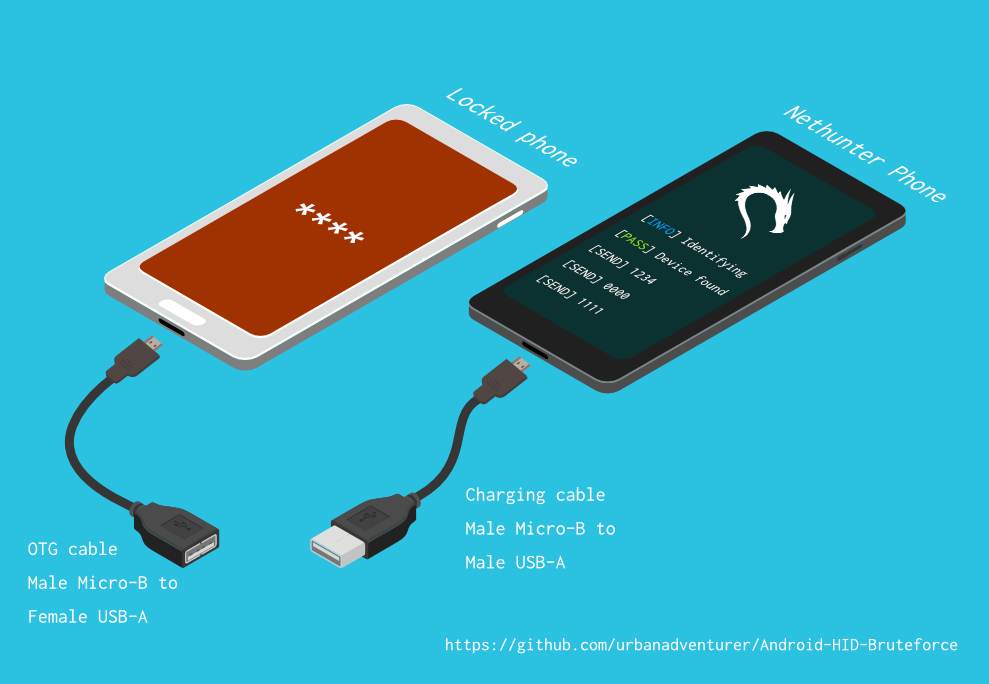
Android-PIN-Bruteforce utilizes a USB OTG cable to connect the locked phone to the Nethunter device. It emulates a keyboard, automatically tries PINs, and waits after attempting too many wrong guesses.
[Nethunter phone] <--> [USB cable] <--> [USB OTG adaptor] <--> [Locked Android phone]
The USB HID Gadget driver provides emulation of USB Human Interface Devices (HID). This enables an Android Nethunter device to emulate keyboard input to the locked phone, simulating plugging a keyboard into the locked phone and pressing keys.
⏱ With a Samsung S5, it takes just over 16.6 hours to try all possible 4-digit PINs, but with the optimized PIN list, it should take much less time.
- A locked Android phone
- A Nethunter phone (or any rooted Android with HID kernel support)
- USB OTG (On The Go) cable/adapter (USB male Micro-B to female USB A) and a standard charging cable (USB male Micro-B to male A)
- Turn your NetHunter phone into an Android PIN cracking machine
- No need for ADB or USB debugging enabled on the locked phone
- The locked Android phone does not need to be rooted
- No need to buy special hardware (e.g., Rubber Ducky, Teensy, Cellebrite, XPIN Clip, etc.)
- Easily modify the backoff time to crack other types of devices
- It works!
- Crack PINs of any length from 1 to 10 digits
- Use config files to support different phones
- Optimized PIN lists for 3, 4, 5, and 6 digit PINs
- Bypass phone pop-ups including the Low Power warning
- Detect when the phone is unplugged or powered off, and wait while retrying every 5 seconds
- Configurable delays after every X PIN attempts
- Log file
TBC
If you installed the script to /sdcard/, you can execute it with the following command.
./android-pin-bruteforceNote: Android mounts /sdcard with the noexec flag. You can verify this with mount.
Android-PIN-Bruteforce (0.2) is used to unlock an Android phone (or device) by bruteforcing the lockscreen PIN.
Find more information at: https://github.com/urbanadventurer/Android-PIN-Bruteforce
Commands:
crack Begin cracking PINs
resume Resume from a chosen PIN
rewind Crack PINs in reverse from a chosen PIN
diag Display diagnostic information
version Display version information and exit
Options:
-f, --from PIN Resume from this PIN
-a, --attempts Starting from NUM incorrect attempts
-m, --mask REGEX Use a mask for known digits in the PIN
-t, --type TYPE Select PIN or PATTERN cracking
-l, --length NUM Crack PINs of NUM length
-c, --config FILE Specify configuration file to load
-p, --pinlist FILE Specify a custom PIN list
-d, --dry-run Dry run for testing. Doesn't send any keys.
-v, --verbose Output verbose logs
Usage:
android-pin-bruteforce <command> [options]
Successfully tested with various phones including Samsung S5, S7, Motorola G4 Plus, and G5 Plus.
It can unlock Android versions 6.0.1 through 10.0. The ability to perform a bruteforce attack doesn't depend on the Android version but on how the device vendor developed their lockscreen.
Check the Phone Database for more details: Phone Database
Optimized PIN lists are used by default unless a custom PIN list is selected.
Use the --length command-line option.
- To crack a 3-digit PIN:
./android-pin-bruteforce crack --length 3 - To crack a 6-digit PIN:
./android-pin-bruteforce crack --length 6
The optimized PIN lists were generated from Ga$$Pacc DB Leak and mandatoryprogrammer's GitHub repository.
The 4-digit PIN list comes from Justin Engler & Paul Vines from Senior Security Engineer, iSEC Partners, used in their Defcon talk.
Masks use regular expressions with the standard grep extended format.
./android-pin-bruteforce crack --mask "...[45]" --dry-run
Device manufacturers create their own lock screens. To find out what keys your phone needs, plug a keyboard into the phone and try out different combinations.
Load a different configuration file with the --config FILE command-line parameter.
Example: ./android-pin-bruteforce --config ./config.samsung.s5 crack
You can also edit the config file by customizing the timing and keys sent.
We send keys before the end of the cooldown period or optionally during the cooldown period to keep the lockscreen app active and to dismiss any popups about the number of incorrect PIN attempts or a low battery warning.
Use SSH from your laptop to the NetHunter phone and use this command to test sending keys:
In this example, the enter key is sent.
echo "enter" | /system/xbin/hid-keyboard /dev/hidg0 keyboard
Use this Android app, a virtual USB Keyboard, to test sending keys: Remote HID Keyboard Client
Refer to the provided list in the readme for sending special keys.
Check the readme for troubleshooting steps.
Check the readme for known issues.
Check the readme for the project's roadmap.
Pull requests are welcome. For major changes, please open an issue first to discuss what you would like to change.
Developed by Andrew Horton (@urbanadventurer).
👏 The following people have been very helpful:
- Vlad Filatov (@v1adf): Testing many phones for the Wiki
, adding new masks, and providing additional feedback.
- Gabriele Corrado (@GabrieleCM): Providing additional feedback and testing.
- Aleksejs Popovs (@aleksejspopovs): Providing feedback and testing.
- Ghee (@ghee22): Providing feedback and testing.
- Shimon Das (@shimon835): Providing feedback and testing.
- Henry (@hexatrope): Providing feedback and testing.
- Maksim (@maaaaksym): Testing and providing feedback.
Check the readme for more details and information.
This script is powerful and versatile, but please use it responsibly and legally. Unauthorized access to someone else's device without permission is illegal and unethical. Always obtain proper authorization before attempting to unlock any device.