This repository is no longer supported, please consider using this repository for the latest and most supported version for Vault.
Moving forward in the future this repository will be no longer supported and eventually lead to deprecation. Please use our latest versions of our products moving forward or alternatively you may fork the repository to continue use and development for your personal/business use.
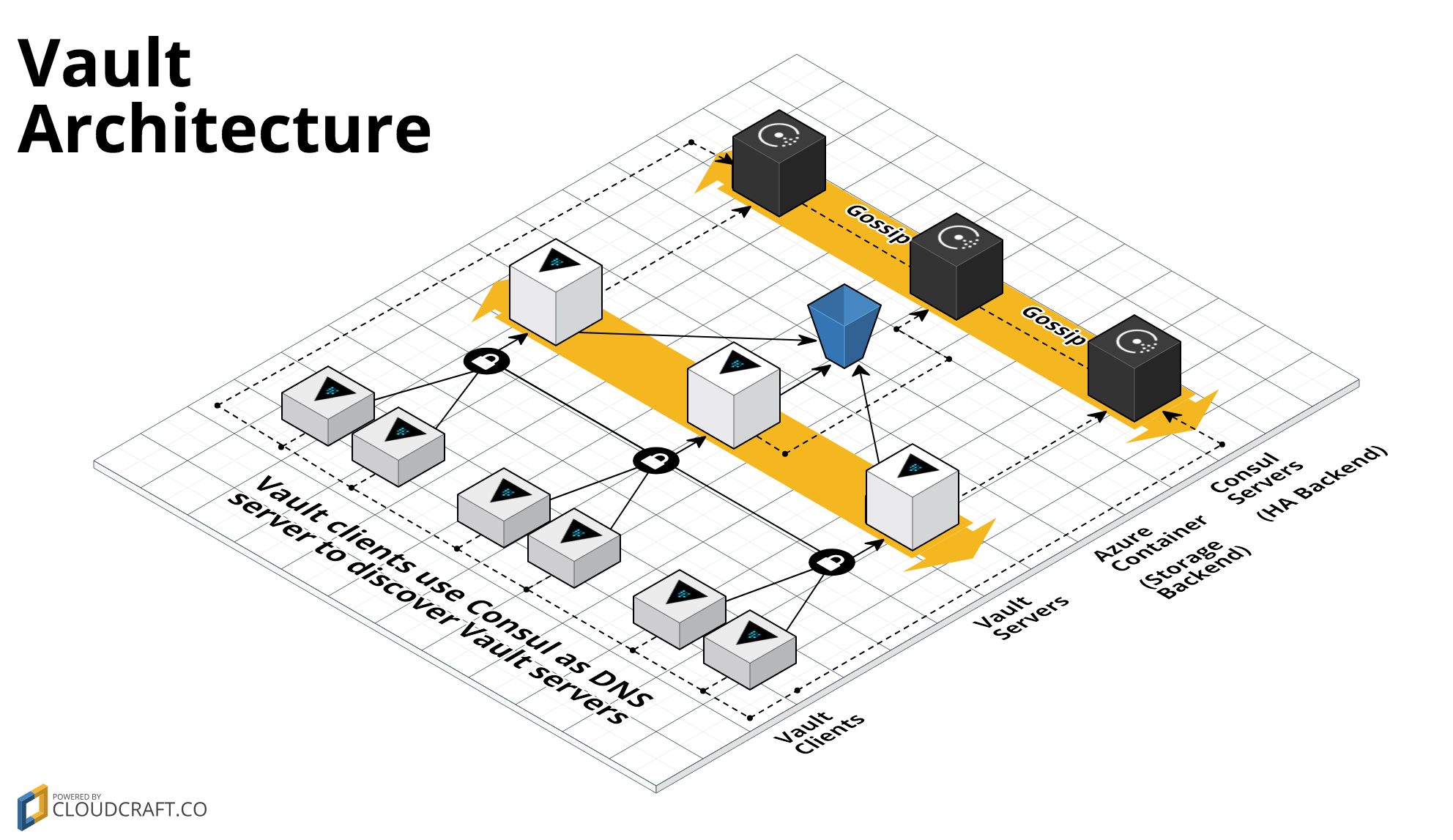
This repo contains a Module to deploy a Vault cluster on Azure using Terraform. Vault is an open source tool for managing secrets. This Module uses Azure Storage as a storage backend and a Consul server cluster as a high availability backend:
This Module includes:
-
install-vault: This module can be used to install Vault. It can be used in a Packer template to create a Vault Azure Manager Image.
-
run-vault: This module can be used to configure and run Vault. It can be used in a Custom Data script to fire up Vault while the server is booting.
-
vault-cluster: Terraform code to deploy a cluster of Vault servers using an [Scale Set] (https://docs.microsoft.com/en-us/azure/virtual-machine-scale-sets/virtual-machine-scale-sets-create).
-
private-tls-cert: Generate a private TLS certificate for use with a private Vault cluster.
-
update-certificate-store: Add a trusted, CA public key to an OS's certificate store. This allows you to establish TLS connections to services that use this TLS certs signed by this CA without getting x509 certificate errors.
A Module is a canonical, reusable, best-practices definition for how to run a single piece of infrastructure, such as a database or server cluster. Each Module is created primarily using Terraform, includes automated tests, examples, and documentation, and is maintained both by the open source community and companies that provide commercial support.
Instead of having to figure out the details of how to run a piece of infrastructure from scratch, you can reuse existing code that has been proven in production. And instead of maintaining all that infrastructure code yourself, you can leverage the work of the Module community and maintainers, and pick up infrastructure improvements through a version number bump.
These modules were created by Gruntwork, in partnership with HashiCorp, in 2017 and maintained through 2021. They were deprecated in 2022 in favor of newer alternatives (see the top of the README for details).
Each Module has the following folder structure:
- root: The root folder contains an example of running a public Vault cluster on Azure
- modules: This folder contains the reusable code for this Module, broken down into one or more modules.
- examples: This folder contains examples of how to use the modules.
- test: Automated tests for the modules and examples.
Click on each of the modules above for more details.
To deploy Vault with this Blueprint, you will need to deploy two separate clusters: one to run Consul servers (which Vault uses as a high availability backend) and one to run Vault servers.
To deploy the Consul server cluster, use the Consul Azure Module.
To deploy the Vault cluster:
-
Create an Azure Image that has Vault installed (using the install-vault module) and the Consul agent installed (using the install-consul module). Here is an example Packer template.
-
Deploy that Azure Image across a Scale Set in a private subnet using the Terraform vault-cluster module.
-
Execute the run-consul script with the
--clientflag during boot on each Instance to have the Consul agent connect to the Consul server cluster. -
Execute the run-vault script during boot on each Instance to create the Vault cluster.
-
If you only need to access Vault from inside your Azure account (recommended), run the install-dnsmasq module on each server, and that server will be able to reach Vault using the Consul Server cluster as the DNS resolver (e.g. using an address like
vault.service.consul). See the main example for working sample code. -
Head over to the How do you use the Vault cluster? guide to learn how to initialize, unseal, and use Vault.
This Module follows the principles of Semantic Versioning. You can find each new release, along with the changelog, in the Releases Page.
During initial development, the major version will be 0 (e.g., 0.x.y), which indicates the code does not yet have a
stable API. Once we hit 1.0.0, we will make every effort to maintain a backwards compatible API and use the MAJOR,
MINOR, and PATCH versions on each release to indicate any incompatibilities.
This code is released under the Apache 2.0 License. Please see LICENSE and NOTICE for more details.