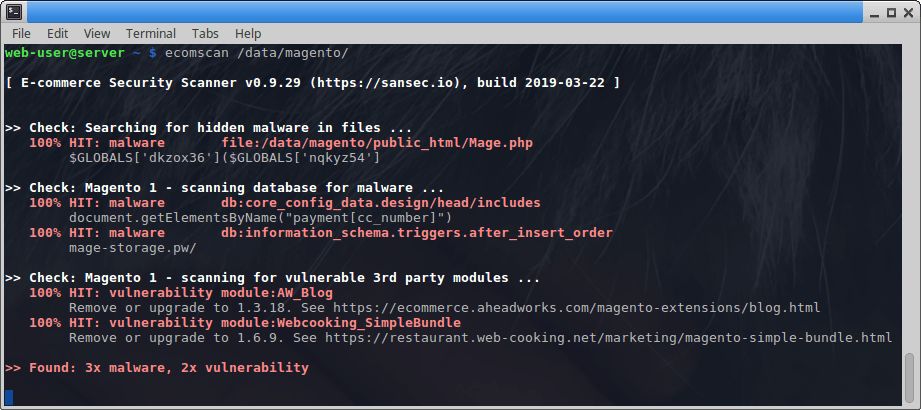
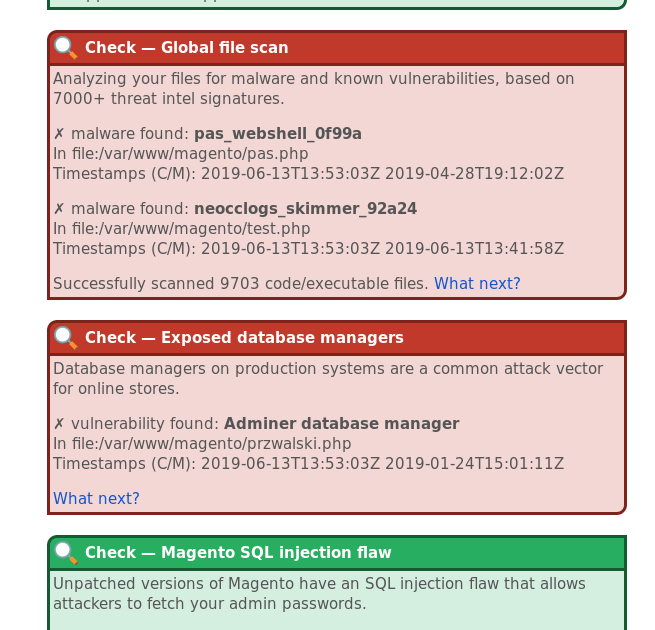
eComscan is the mwscan successor and we recommend everyone to upgrade. Scan your system in 5 minutes. Run this command in a SSH terminal:
curl https://ecomscan.com | sh
Read more about eComscan. It is developed by Sansec, experts in Magento store security and Adobe Commerce security partner.
- 50 thousand malware signatures and counting
- Detects vulnerabilities in popular ecommerce platforms (Magento, Woocommerce, Prestashop etc) and third party ecommerce components
- Monitoring of files, databases, processes, cron...
- Get instant, actionable alerts via mail, Slack or API webhook
The Sansec threat intel team investigates hundreds of hacked stores per month, and adds new attack signatures multiple times per day. eComscan is the best solution to protect your Magento store from emerging threats.
Mwscan and its successor eComscan are used by Adobe, the US Department of Homeland Security, the Magento Marketplace, Magereport and many of the global top ecommerce agencies.
Online payment skimming (aka MageCart) is a growing threat to digital stores. Since our first publication in 2015, we identified more than 90.000 compromised stores. In most cases, malware is inserted that will a) intercept customer data, b) divert payments or c) uses your customers for cryptojacking.
Privacy watchdogs and online regulators are increasingly handing out fines to companies who suffered a Magecart attack.