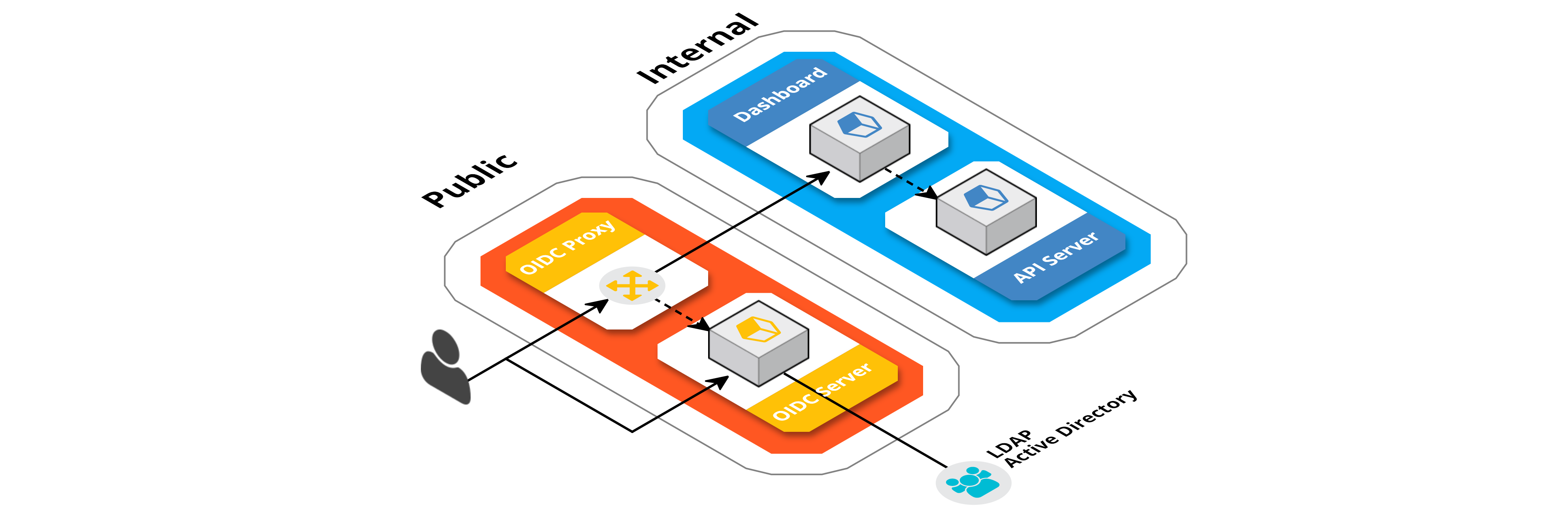
Docker Image for OpenID Connect proxy authentication. Useful for putting services behind Keycloak and other OpenID Connect authentication.
This is Image used Nginx for proxying request and OpenResty with the
lua-resty-openidc library to handle OpenID Connect authentication.
This proxy is controlled through environment variables, so there is no need to mess with any configuration files unless you want to of course. The following environment variables is used in this image:
-
OID_SESSION_SECRET: secret value for cookie sessions -
OID_SESSION_CHECK_SSI: check SSI or not (onoroff) -
OID_SESSION_NAME: cookie session name -
OID_REDIRECT_PATH: Redirect path after authentication -
OID_DISCOVERY: OpenID provider well-known discovery URL -
OID_CLIENT_ID: OpenID Client ID -
OID_CLIENT_SECRET: OpenID Client Secret -
OID_USE_PKCE: Enable PKCE (trueorfalse, default isfalse) -
OIDC_AUTH_METHOD: OpenID Connect authentication method (client_secret_basicorclient_secret_post) -
OIDC_RENEW_ACCESS_TOKEN_ON_EXPIRY: Enable silent renew of access token (trueorfalse) -
PROXY_HOST: Host name of the service to proxy -
PROXY_PORT: Port of the service to proxy -
PROXY_PROTOCOL: Protocol to the service to proxy (httporhttps) -
ADD_HOST_HEADER: pass the proxy host header downstream (trueorfalse)
docker run \
-e OID_DISCOVERY=https://my-auth-server/auth \
-e OID_CLIENT_ID=my-client \
-e OID_CLIENT_SECRET=my-secret \
-e PROXY_HOST=my-service \
-e PROXY_PORT=80 \
-e PROXY_PROTOCOL=http \
-p 80:80 \
evry/oidc-proxy
This Docker image is licensed under the MIT License.
Software contained in this image is licensed under the following:
- docker-openresty: BSD 2-clause "Simplified" License
- lua-resty-http: BSD 2-clause "Simplified" License
- lua-resty-jwt: Apache License 2.0
- lua-resty-openidc: Apache License 2.0
- lua-resty-session: BSD 2-clause "Simplified" License
- lua-resty-hmac: BSD 2-clause "Simplified" License
This image is officially supported on Docker version 1.12.
Support for older versions (down to 1.0) is provided on a best-effort basis.
If you have any problems with or questions about this image, please contact us through a GitHub issue.
You are invited to contribute new features, fixes, or updates, large or small; we are always thrilled to receive pull requests, and do our best to process them as fast as we can.
Before you start to code, we recommend discussing your plans through a GitHub issue, especially for more ambitious contributions. This gives other contributors a chance to point you in the right direction, give you feedback on your design, and help you find out if someone else is working on the same thing.