4
checkmarxdemo's Introduction
checkmarxdemo's People
checkmarxdemo's Issues
CVE-2021-28235 @ Go-go.etcd.io/etcd/server/v3-v3.5.0
Vulnerable Package issue exists @ Go-go.etcd.io/etcd/server/v3-v3.5.0 in branch main
An authentication vulnerability found in Etcd-io in version 3.4.10 through 3.4.24 and v3.5.0-alpha.0 through 3.5.7 allows remote attackers to escalate privileges via the "debug" function.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-287
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: HIGH
Availability impact: HIGH
References
Advisory
Pull request
Commit
Pull request
Commit
CVE-2017-1000048 @ Npm-qs-6.0.0
Vulnerable Package issue exists @ Npm-qs-6.0.0 in branch main
the web framework using ljharb's qs module older than v6.3.2, v6.2.3, v6.1.2, and v6.0.4 is vulnerable to a DoS. A malicious user can send a evil request to cause the web framework crash.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-20
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: NONE
Availability impact: HIGH
Remediation Upgrade Recommendation: 6.2.4
References
Commit
Commit
Advisory
Advisory
Issue
Pull request
Pull request
Cxcc09496a-59c8 @ Npm-js-yaml-3.6.1
Vulnerable Package issue exists @ Npm-js-yaml-3.6.1 in branch main
js-yaml is vulnerable to Code Injection before 3.13.1. The load() function may execute arbitrary code injected through a malicious YAML file. Objects that have "toString" as key and JavaScript code as value are used as explicit mapping keys, this allows attackers to execute the supplied code through the load() function. The safeLoad() function is unaffected.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-94
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: HIGH
Availability impact: HIGH
Remediation Upgrade Recommendation: 3.13.1
References
Issue
Pull request
Commit
Advisory
Apt Get Install Pin Version Not Defined @ /Dockerfile
Apt Get Install Pin Version Not Defined issue exists @ Dockerfile in branch main
When installing a package, its pin version should be defined
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
Cx68e4da20-b53a @ Npm-ua-parser-js-0.7.29
Vulnerable Package issue exists @ Npm-ua-parser-js-0.7.29 in branch main
This package exfiltrates stored credentials and sensitive information
About
Data exfiltration may be done in numerous ways such as through HTTP requests, DNS tunneling, various webhooks and more. It is common by attackers to try to exfiltrate sensitive information such as:
- Credentials
- Environment variables
- SSH keys
- Authentication tokens
- Computer and operating system information
- Network settings
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
Cxec49316b-56df @ Npm-js-yaml-3.6.1
Vulnerable Package issue exists @ Npm-js-yaml-3.6.1 in branch main
The package js-yaml before 3.13.0 is vulnerable to Denial of service as the function storeMappingPair() in file lib/js-yaml/loader.js, doesn't limit the user supplied yaml, causing the map key to grow exponentially. giving out a huge amount of output data, leading to denial of service due to excessive memory usage. This affects the availability.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-674
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: NONE
Availability impact: HIGH
Remediation Upgrade Recommendation: 3.13.1
Cx3cf24ca3-dd23 @ Npm-ua-parser-js-0.7.29
Vulnerable Package issue exists @ Npm-ua-parser-js-0.7.29 in branch main
This package exfiltrates computer and operating system information
About
Data exfiltration may be done in numerous ways such as through HTTP requests, DNS tunneling, various webhooks and more. It is common by attackers to try to exfiltrate sensitive information such as:
- Credentials
- Environment variables
- SSH keys
- Authentication tokens
- Computer and operating system information
- Network settings
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
Additional Info
Cx0a21eeca-49b1 @ Npm-scs-0.0.1
Vulnerable Package issue exists @ Npm-scs-0.0.1 in branch main
This package exfiltrates stored credentials and sensitive information
About
Data exfiltration may be done in numerous ways such as through HTTP requests, DNS tunneling, various webhooks and more. It is common by attackers to try to exfiltrate sensitive information such as:
- Credentials
- Environment variables
- SSH keys
- Authentication tokens
- Computer and operating system information
- Network settings
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
Shield Advanced Not In Use @ /terraform_examples/negative1.tf
Shield Advanced Not In Use issue exists @ negative1.tf in branch main
AWS Shield Advanced should be used for Amazon Route 53 hosted zone, AWS Global Accelerator accelerator, Elastic IP Address, Elastic Load Balancing, and Amazon CloudFront Distribution to protect these resources against robust DDoS attacks
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: LOW
State: TO_VERIFY
Status: RECURRENT
CVE-2022-41717 @ Go-golang.org/x/net-v0.0.0-20220225172249-27dd8689420f
Vulnerable Package issue exists @ Go-golang.org/x/net-v0.0.0-20220225172249-27dd8689420f in branch main
An attacker can cause excessive memory growth in a Go server accepting HTTP/2 requests. HTTP/2 server connections contain a cache of HTTP header keys sent by the client. While the total number of entries in this cache is capped, an attacker sending very large keys can cause the server to allocate approximately 64 MiB per open connection. This issue affects "golang.org/x/net" package versions prior to v0.4.0.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-770
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: NONE
Availability impact: LOW
References
Advisory
Commit
Advisory
Release Note
Mail Thread
Issue
CVE-2022-23305 @ Maven-log4j:log4j-1.2.17
Vulnerable Package issue exists @ Maven-log4j:log4j-1.2.17 in branch main
By design, the JDBCAppender in Log4j 1.2.x accepts an SQL statement as a configuration parameter where the values to be inserted are converters from PatternLayout. The message converter, %m, is likely to always be included. This allows attackers to manipulate the SQL by entering crafted strings into input fields or headers of an application that are logged allowing unintended SQL queries to be executed. Note this issue only affects Log4j 1.x when specifically configured to use the JDBCAppender, which is not the default. Beginning in version 2.0-beta8, the JDBCAppender was re-introduced with proper support for parameterized SQL queries and further customization over the columns written to in logs. Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-89
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: HIGH
Availability impact: HIGH
Remediation Upgrade Recommendation: 1.2.17-atlassian-0.4
References
Advisory
Mail Thread
Advisory
Cx8147ddef-ae09 @ Python-azure-powerbiembedded-6969.99.99
Vulnerable Package issue exists @ Python-azure-powerbiembedded-6969.99.99 in branch main
This package was manually inspected by a security researcher and flagged as malicious
About
Classifying malicious packages is an internal process, analysis is done at scale automatically via multiple engines. Once there's a risk suspicion, this is forwarded to a security researcher for a manual evaluation.
Attackers take advantage of the excessive trust in the open-source ecosystem and launch software supply chain attacks in the form of code packages.
The risk of having a package with a malicious payload is high. It's a common behavior for most of the malicious payloads to execute itself automatically upon installing or using the package.
While some dependency vulnerabilities have the privilege to be kept as known issue due to risk-management, same does not apply in the case of a malicious package, and it should be removed with the highest priority.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
CVE-2022-22976 @ Maven-org.springframework.security:spring-security-core-3.2.4.RELEASE
Vulnerable Package issue exists @ Maven-org.springframework.security:spring-security-core-3.2.4.RELEASE in branch main
Spring Security, modules "spring-security-core" and "spring-security-crypto", versions 5.5.x prior to 5.5.7, 5.6.x prior to 5.6.4, and earlier unsupported versions contain an integer overflow vulnerability. When using the "BCrypt" class with the maximum work factor (31), the encoder does not perform any salt rounds, due to an integer overflow error. The default settings are not affected by this CVE.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-190
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: LOW
Availability impact: NONE
Remediation Upgrade Recommendation: 4.0.0.M2
CVE-2019-3795 @ Maven-org.springframework.security:spring-security-core-3.2.4.RELEASE
Vulnerable Package issue exists @ Maven-org.springframework.security:spring-security-core-3.2.4.RELEASE in branch main
Spring Security before version 4.2.12, 5.0.x prior to 5.0.12, and 5.1.x prior to 5.1.5 contain an insecure randomness vulnerability when using SecureRandomFactoryBean#setSeed to configure a SecureRandom instance. In order to be impacted, an honest application must provide a seed and make the resulting random material available to an attacker for inspection.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-330
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: LOW
Availability impact: NONE
Remediation Upgrade Recommendation: 4.0.0.M2
CVE-2022-23307 @ Maven-log4j:log4j-1.2.17
Vulnerable Package issue exists @ Maven-log4j:log4j-1.2.17 in branch main
CVE-2020-9493 identified a deserialization issue that was present in Apache Chainsaw. Prior to Chainsaw V2.0, Chainsaw was a component of Apache Log4j 1.x where the same issue exists.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-502
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: HIGH
Availability impact: HIGH
Remediation Upgrade Recommendation: 1.2.17-atlassian-0.4
References
Mail Thread
Issue
Advisory
Advisory
Cxfd197ca1-b64b @ Npm-momnet-2.29.1
Vulnerable Package issue exists @ Npm-momnet-2.29.1 in branch main
This package was manually inspected by a security researcher and flagged as malicious
About
Classifying malicious packages is an internal process, analysis is done at scale automatically via multiple engines. Once there's a risk suspicion, this is forwarded to a security researcher for a manual evaluation.
Attackers take advantage of the excessive trust in the open-source ecosystem and launch software supply chain attacks in the form of code packages.
The risk of having a package with a malicious payload is high. It's a common behavior for most of the malicious payloads to execute itself automatically upon installing or using the package.
While some dependency vulnerabilities have the privilege to be kept as known issue due to risk-management, same does not apply in the case of a malicious package, and it should be removed with the highest priority.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
EC2 Instance Has Public IP @ /terraform_examples/positive2.tf
EC2 Instance Has Public IP issue exists @ positive2.tf in branch main
EC2 Instance should not have a public IP address.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CVE-2022-1996 @ Go-github.com/emicklei/go-restful-v2.9.5
Vulnerable Package issue exists @ Go-github.com/emicklei/go-restful-v2.9.5 in branch main
Authorization Bypass Through User-Controlled Key in emicklei/go-restful prior to v3.8.0.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-639
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: HIGH
Availability impact: NONE
References
Advisory
Advisory
Disclosure
Issue
Commit
Pull request
EC2 Instance Has Public IP @ /terraform_examples/negative2.tf
EC2 Instance Has Public IP issue exists @ negative2.tf in branch main
EC2 Instance should not have a public IP address.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Cx9f739bef-35bb @ Npm-flow-dev-tools-99.10.9
Vulnerable Package issue exists @ Npm-flow-dev-tools-99.10.9 in branch main
This package is using dependency confusion attack
About
Dependency Confusion is a technique discovered by @alex.birsan to hijack a privately used package by registering its name (if available) on a public registry with a higher version number. This may cause artifact servers and build tools to "confuse" and use the attacker's package.
For example, consider the following private package "my-company-utils" being hosted on a private artifact server:
In case an attacker targeting "my-company-utils" package, as long as it is not occupied by someone else on the official package manager, he's free to register it. If the attacker registers it and published with a very high version number such as "v99.99.99" most likely the automatic update logic and version comparisons functions will "confuse" and prefer using the attacker's package
As an addition step of mitigation, we recommend using our open-source tool as a CI step DustiLock
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
CVE-2019-10744 @ Npm-lodash-4.17.11
Vulnerable Package issue exists @ Npm-lodash-4.17.11 in branch main
A Prototype Pollution vulnerability was discovered in lodash before 4.17.12, in lodash.defaultsdeep before 4.6.1 and in @sailshq/lodash before 3.10.4. The function defaultsDeep allows a malicious user to modify the prototype of Object via {constructor: {prototype: {...}}} causing the addition or modification of an existing property that will exist on all objects.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-1321
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: NONE
Availability impact: HIGH
Remediation Upgrade Recommendation: 4.17.21
References
Disclosure
Advisory
Pull request
Commit
Commit
Advisory
Advisory
Cxba768ce4-aa4e @ Npm-node-ipc-9.2.2
Vulnerable Package issue exists @ Npm-node-ipc-9.2.2 in branch main
The Contributor of this package, npm user riaevangelist, previously seen corrupting one of his popular package node-ipc infected with a malicious payload. Read more
About
We recommend freezing this package's version in your manifest file or consider finding an alternative to this package.
Relying on code from an unreliable contributors could damage the integrity of the code built depends on it. There is a risk this package may be corrupted as well in future versions.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
Additional Info
ALB Not Dropping Invalid Headers @ /terraform_examples/positive2.tf
ALB Not Dropping Invalid Headers issue exists @ positive2.tf in branch main
It's considered a best practice when using Application Load Balancers to drop invalid header fields
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
Cx743605c8-a95e @ Npm-momnet-2.29.1
Vulnerable Package issue exists @ Npm-momnet-2.29.1 in branch main
There is a weak link between the package's listed metadata and the referenced Git repository "https://github.com/moment/moment"
About
Package managers often display traction statistics per code package based on it's related GitHub repository. This statistics helps developers to evaluate code packages.
The statistics displayed by the package managers do not go through any validation process. It can easily be falsified to mislead developers because of how this information is acquired.
As part of the package metadata analysis capabilities Checkmarx has, StarJacking engine verifies the authenticity of such Git repository references and in case it's a false reference, this risk is shown
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
Additional Info
Cxbec87a55-fe55 @ Npm-node-ipc-9.2.2
Vulnerable Package issue exists @ Npm-node-ipc-9.2.2 in branch main
This package was manually inspected by a security researcher and flagged as malicious
About
Classifying malicious packages is an internal process, analysis is done at scale automatically via multiple engines. Once there's a risk suspicion, this is forwarded to a security researcher for a manual evaluation.
Attackers take advantage of the excessive trust in the open-source ecosystem and launch software supply chain attacks in the form of code packages.
The risk of having a package with a malicious payload is high. It's a common behavior for most of the malicious payloads to execute itself automatically upon installing or using the package.
While some dependency vulnerabilities have the privilege to be kept as known issue due to risk-management, same does not apply in the case of a malicious package, and it should be removed with the highest priority.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
ALB Not Dropping Invalid Headers @ /terraform_examples/negative2.tf
ALB Not Dropping Invalid Headers issue exists @ negative2.tf in branch main
It's considered a best practice when using Application Load Balancers to drop invalid header fields
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
CVE-2022-22970 @ Maven-org.springframework:spring-core-3.2.4.RELEASE
Vulnerable Package issue exists @ Maven-org.springframework:spring-core-3.2.4.RELEASE in branch main
In Spring Framework versions 5.2.0 through 5.2.21, 5.3.0 through 5.3.19, and older unsupported versions, applications that handle file uploads are vulnerable to DoS attacks if they rely on data binding to set a "MultipartFile" or "javax.servlet.Part" to a "field" in a model object.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-770
Additional Info
Attack vector: NETWORK
Attack complexity: HIGH
Confidentiality impact: NONE
Availability impact: HIGH
Remediation Upgrade Recommendation: 4.0.0.M3
References
Advisory
Advisory
Blog Post
Release Note
Commit
Issue
Missing User Instruction @ /Dockerfile
Missing User Instruction issue exists @ Dockerfile in branch main
A user should be specified in the dockerfile, otherwise the image will run as root
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: RECURRENT
CVE-2022-28948 @ Go-gopkg.in/yaml.v3-v3.0.0-20210107192922-496545a6307b
Vulnerable Package issue exists @ Go-gopkg.in/yaml.v3-v3.0.0-20210107192922-496545a6307b in branch main
An issue in the "Unmarshal" function in gopkg.in/yaml.v3 and github.com/go-yaml/yaml versions prior to v3.0.0-20220521103104-8f96da9f5d5e causes the program to crash when attempting to deserialize invalid input.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-502
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: NONE
Availability impact: HIGH
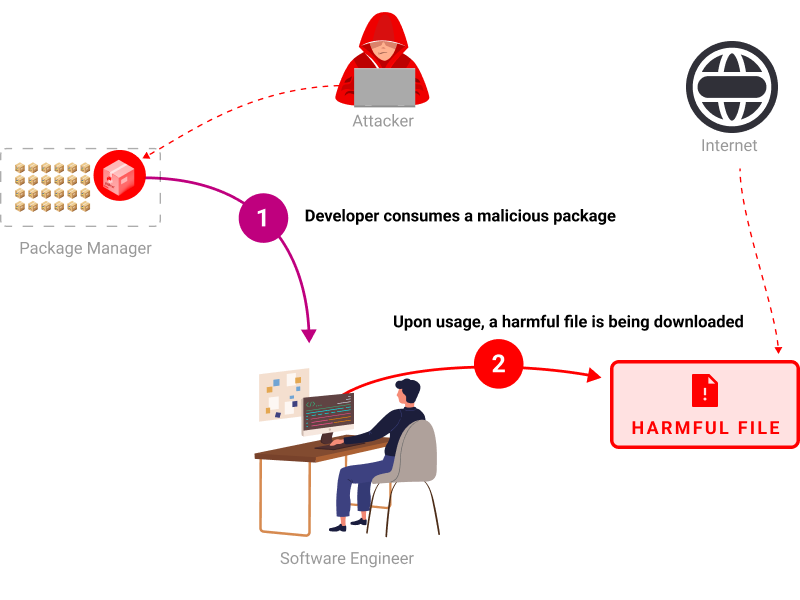
Cx8079a3fb-ff1f @ Npm-ua-parser-js-0.7.29
Vulnerable Package issue exists @ Npm-ua-parser-js-0.7.29 in branch main
This package downloads a harmful file.
File hash:
7f986cd3c946f274cdec73f80b84855a77bc2a3c765d68897fbc42835629a5d5
About
Using a dynamic analysis environment (also known as a Sandbox) we can monitor filesystem activity such as newly created files within the lifecycle of the code package.
Once new files are created, our technology analyzes each of the newly created files. In case a file is harmful, this risk is shown.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
Cx18e041aa-8a63 @ Npm-node-ipc-9.2.2
Vulnerable Package issue exists @ Npm-node-ipc-9.2.2 in branch main
The malicious payload in this package has the ability to corrupt or destroy files on disk
About
File wiping or file destruction is a type of risk which usually done when attackers wish to cause harm. File destruction can be done in several ways such as:
- Recursively overwriting all files with random / static content
- Deleting all files
- Encrypting all files and deleting the encryption key
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
CVE-2022-22968 @ Maven-org.springframework:spring-context-3.2.8.RELEASE
Vulnerable Package issue exists @ Maven-org.springframework:spring-context-3.2.8.RELEASE in branch main
In Spring Framework versions before 5.2.2.RELEASE, and 5.3.0 through 5.3.18, and older unsupported versions, the patterns for disallowedFields on a DataBinder are case sensitive which means a field is not effectively protected unless it is listed with both upper and lower case for the first character of the field, including upper and lower case for the first character of all nested fields within the property path.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-178
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: NONE
Availability impact: NONE
Remediation Upgrade Recommendation: 4.1.0.RC1
CVE-2021-4229 @ Npm-ua-parser-js-0.7.29
Vulnerable Package issue exists @ Npm-ua-parser-js-0.7.29 in branch main
A vulnerability was found in ua-parser-js 0.7.29, 0.8.0, and 1.0.0. It has been rated as critical. This issue affects the crypto mining component which introduces a backdoor. Upgrading to version 0.7.30, 0.8.1 and 1.0.1 is able to address this issue. It is recommended to upgrade the affected component.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-829
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: HIGH
Availability impact: HIGH
Remediation Upgrade Recommendation: 0.7.33
CVE-2022-25927 @ Npm-ua-parser-js-0.7.29
Vulnerable Package issue exists @ Npm-ua-parser-js-0.7.29 in branch main
Versions of the package ua-parser-js 0.7.30 through 0.7.32, and 0.8.1 through 1.0.32 are vulnerable to Regular Expression Denial of Service (ReDoS) via the "trim()" function.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-1333
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: NONE
Availability impact: HIGH
Remediation Upgrade Recommendation: 0.7.33
Cx0eb7d3da-c52e @ Python-azure-powerbiembedded-6969.99.99
Vulnerable Package issue exists @ Python-azure-powerbiembedded-6969.99.99 in branch main
This package communicates with a suspicious service commonly used by threat actors
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
Cx0b915a4a-2d97 @ Npm-scs-0.0.1
Vulnerable Package issue exists @ Npm-scs-0.0.1 in branch main
This package downloads a harmful file.
File hash:
2a3acdcd76575762b18c18c644a745125f55ce121f742d2aad962521bc7f25fd
About
Using a dynamic analysis environment (also known as a Sandbox) we can monitor filesystem activity such as newly created files within the lifecycle of the code package.
Once new files are created, our technology analyzes each of the newly created files. In case a file is harmful, this risk is shown.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
Cx4ca27ec0-0c96 @ Npm-scs-0.0.1
Vulnerable Package issue exists @ Npm-scs-0.0.1 in branch main
This package downloads a harmful file.
File hash:
7f986cd3c946f274cdec73f80b84855a77bc2a3c765d68897fbc42835629a5d5
About
Using a dynamic analysis environment (also known as a Sandbox) we can monitor filesystem activity such as newly created files within the lifecycle of the code package.
Once new files are created, our technology analyzes each of the newly created files. In case a file is harmful, this risk is shown.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
CVE-2022-21698 @ Go-github.com/prometheus/client_golang-v1.11.0
Vulnerable Package issue exists @ Go-github.com/prometheus/client_golang-v1.11.0 in branch main
client_golang is the instrumentation library for Go applications in Prometheus, and the promhttp package in client_golang provides tooling around HTTP servers and clients. In client_golang prior to version 1.11.1, HTTP server is susceptible to a Denial of Service through unbounded cardinality, and potential memory exhaustion, when handling requests with non-standard HTTP methods. In order to be affected, an instrumented software must use any of promhttp.InstrumentHandler* middleware except RequestsInFlight; not filter any specific methods (e.g GET) before middleware; pass metric with method label name to our middleware; and not have any firewall/LB/proxy that filters away requests with unknown method. client_golang version 1.11.1 contains a patch for this issue. Several workarounds are available, including removing the method label name from counter/gauge used in the InstrumentHandler; turning off affected promhttp handlers; adding custom middleware before promhttp handler that will sanitize the request method given by Go http.Request; and using a reverse proxy or web application firewall, configured to only allow a limited set of methods.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-772
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: NONE
Availability impact: HIGH
References
Advisory
Advisory
Pull request
Commit
Release Note
CVE-2022-23302 @ Maven-log4j:log4j-1.2.17
Vulnerable Package issue exists @ Maven-log4j:log4j-1.2.17 in branch main
JMSSink in all versions of Log4j 1.x is vulnerable to deserialization of untrusted data when the attacker has write access to the Log4j configuration or if the configuration references an LDAP service the attacker has access to. The attacker can provide a TopicConnectionFactoryBindingName configuration causing JMSSink to perform JNDI requests that result in remote code execution in a similar fashion to CVE-2021-4104. Note this issue only affects Log4j 1.x when specifically configured to use JMSSink, which is not the default. Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-502
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: HIGH
Availability impact: HIGH
Remediation Upgrade Recommendation: 1.2.17-atlassian-0.4
References
Advisory
Mail Thread
Advisory
CVE-2022-22950 @ Maven-org.springframework:spring-core-3.2.4.RELEASE
Vulnerable Package issue exists @ Maven-org.springframework:spring-core-3.2.4.RELEASE in branch main
In Spring Framework versions 5.3.0 through 5.3.16, and older unsupported versions, it is possible for a user to provide a specially crafted SpEL expression that may cause a denial of service condition.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-770
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: NONE
Availability impact: HIGH
Remediation Upgrade Recommendation: 4.0.0.M3
References
Advisory
Advisory
Blog Post
Release Note
Issue
Commit
Cx7401d0a9-2786 @ Npm-ua-parser-js-0.7.29
Vulnerable Package issue exists @ Npm-ua-parser-js-0.7.29 in branch main
This package downloads a harmful file.
File hash:
ea131cc5ccf6aa6544d6cb29cdb78130feed061d2097c6903215be1499464c2e
About
Using a dynamic analysis environment (also known as a Sandbox) we can monitor filesystem activity such as newly created files within the lifecycle of the code package.
Once new files are created, our technology analyzes each of the newly created files. In case a file is harmful, this risk is shown.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
Cxf7a33198-8ff8 @ Npm-node-ipc-9.2.2
Vulnerable Package issue exists @ Npm-node-ipc-9.2.2 in branch main
This package includes functionality which aims to protest or raise an issue and might include undesired behavior.
About
Similar to a malicious package risk, Protestware risk may include malicious functionality as seen in past incidents. Protestware may contain any of the following:
- Targeted payload
- DOS
- SPAM messages
- Malicious dependencies
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
Additional Info
Cxa45b0853-bee2 @ Npm-momnet-2.29.1
Vulnerable Package issue exists @ Npm-momnet-2.29.1 in branch main
This package name is similar to other popular package "moment"
About
Typosquatting attacks relies on user type errors being inputted into installation commands or manifest files.
For example, let's take the popular npm package moment which has tens of millions of weekly downloads.
A user would like use this package and assisting the npm install command like so:
npm install moment
However, sometimes users tend to do accidentally typos, so another user would write:
npm install momnet
In this case, if a package exists under the Typosquatting name, it will be fetched and used.
Attackers find this method effective and usually tend to copy the original functionality and metadata to avoid detection. Typosquatting is one way to mislead developers to download the wrong package and usually includes with a malicious payloads.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
CVE-2020-15250 @ Maven-junit:junit-4.8.1
Vulnerable Package issue exists @ Maven-junit:junit-4.8.1 in branch main
In JUnit4 from version 4.7 and before 4.13.1, the test rule TemporaryFolder contains a local information disclosure vulnerability. On Unix like systems, the system's temporary directory is shared between all users on that system. Because of this, when files and directories are written into this directory they are, by default, readable by other users on that same system. This vulnerability does not allow other users to overwrite the contents of these directories or files. This is purely an information disclosure vulnerability. This vulnerability impacts you if the JUnit tests write sensitive information, like API keys or passwords, into the temporary folder, and the JUnit tests execute in an environment where the OS has other untrusted users. Because certain JDK file system APIs were only added in JDK 1.7, this this fix is dependent upon the version of the JDK you are using. For Java 1.7 and higher users: this vulnerability is fixed in 4.13.1. For Java 1.6 and lower users: no patch is available, you must use the workaround below. If you are unable to patch, or are stuck running on Java 1.6, specifying the java.io.tmpdir system environment variable to a directory that is exclusively owned by the executing user will fix this vulnerability. For more information, including an example of vulnerable code, see the referenced GitHub Security Advisory.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
CWE: CWE-732
Additional Info
Attack vector: LOCAL
Attack complexity: LOW
Confidentiality impact: HIGH
Availability impact: NONE
Remediation Upgrade Recommendation: 4.13.1
References
Advisory
Release Note
Issue
Commit
Cxb52dba53-66d2 @ Python-not-particularly-2.5.0
Vulnerable Package issue exists @ Python-not-particularly-2.5.0 in branch main
This package communicates with a suspicious service commonly used by threat actors
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: RECURRENT
Additional Info
CVE-2019-17571 @ Maven-log4j:log4j-1.2.17
Vulnerable Package issue exists @ Maven-log4j:log4j-1.2.17 in branch main
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data. This affects Log4j 1.2 up to 1.2.17.
NOTE: log4j:log4j 1.2 is end-of-life since 2015 and will not be fixed.
MITIGATION: Migrate to org.apache.logging.log4j:log4j-core 2.8.2 or above.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
CWE: CWE-502
Additional Info
Attack vector: NETWORK
Attack complexity: LOW
Confidentiality impact: HIGH
Availability impact: HIGH
Remediation Upgrade Recommendation: 1.2.17-atlassian-0.4
References
Mail Thread
Release Note
Issue
Commit
Advisory
VPC Without Network Firewall @ /terraform_examples/positive2.tf
VPC Without Network Firewall issue exists @ positive2.tf in branch main
VPC should have a Network Firewall associated
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
Cx6bee2138-4df0 @ Npm-flow-dev-tools-99.10.9
Vulnerable Package issue exists @ Npm-flow-dev-tools-99.10.9 in branch main
This package was manually inspected by a security researcher and flagged as malicious
About
Classifying malicious packages is an internal process, analysis is done at scale automatically via multiple engines. Once there's a risk suspicion, this is forwarded to a security researcher for a manual evaluation.
Attackers take advantage of the excessive trust in the open-source ecosystem and launch software supply chain attacks in the form of code packages.
The risk of having a package with a malicious payload is high. It's a common behavior for most of the malicious payloads to execute itself automatically upon installing or using the package.
While some dependency vulnerabilities have the privilege to be kept as known issue due to risk-management, same does not apply in the case of a malicious package, and it should be removed with the highest priority.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: RECURRENT
Additional Info
ALB Not Dropping Invalid Headers @ /terraform_examples/negative1.tf
ALB Not Dropping Invalid Headers issue exists @ negative1.tf in branch main
It's considered a best practice when using Application Load Balancers to drop invalid header fields
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 7c4b2830-cd3c-4f07-8ef3-0db21b4eb89d
Branch: main
Application: CheckmarxDemo
Severity: MEDIUM
State: TO_VERIFY
Status: RECURRENT
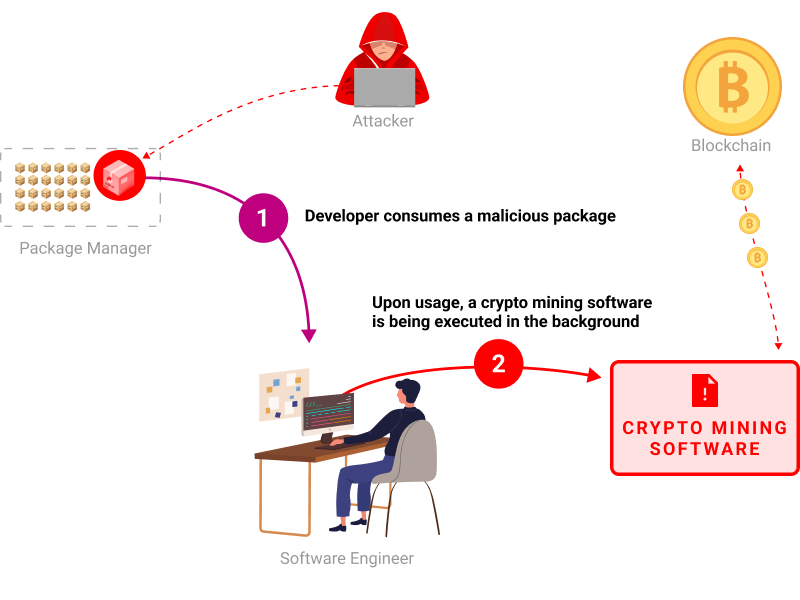
Cxae9d1b09-2adb @ Npm-scs-0.0.1
Vulnerable Package issue exists @ Npm-scs-0.0.1 in branch main
This package executes a crypto mining software
About
Using a dynamic analysis environment (also known as a Sandbox) we can monitor filesystem activity such as newly created files within the lifecycle of the code package.
Once new files are created, our technology analyzes network and filesystem activity. In case a crypto mining behavior is detected, this risk is shown.
Namespace: diogopcx
Repository: CheckmarxDemo
Repository Url: https://github.com/diogopcx/CheckmarxDemo
CxAST-Project: diogopcx/CheckmarxDemo
CxAST platform scan: 40ef948d-8863-4d8b-823b-b512bd2fe1eb
Branch: main
Application: CheckmarxDemo
Severity: HIGH
State: TO_VERIFY
Status: NEW
Additional Info
Recommend Projects
-
 React
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
 Typescript
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
-
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.