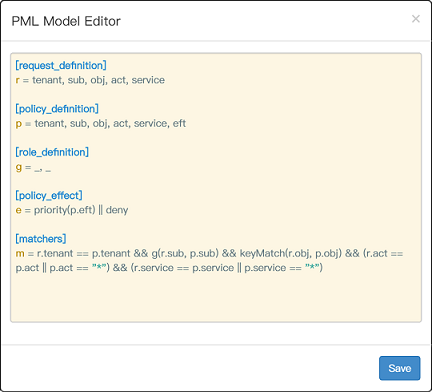
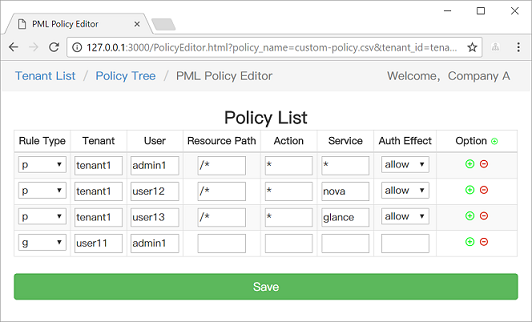
News: still worry about how to write the correct Casbin policy? Casbin online editor is coming to help! Try it at: https://casbin.org/editor/
Casbin-RS is a powerful and efficient open-source access control library for Rust projects. It provides support for enforcing authorization based on various access control models.
 |
 |
 |
 |
|---|---|---|---|
| Casbin | jCasbin | node-Casbin | PHP-Casbin |
| production-ready | production-ready | production-ready | production-ready |
 |
 |
 |
 |
|---|---|---|---|
| PyCasbin | Casbin.NET | Casbin-CPP | Casbin-RS |
| production-ready | production-ready | production-ready | production-ready |
Add this package to Cargo.toml of your project. (Check https://crates.io/crates/casbin for right version)
[dependencies]
casbin = { version = "2.3.0", default-features = false, features = ["runtime-async-std", "logging", "incremental"] }
tokio = { version = "1.10.0", features = ["fs", "io-util"] }Warning: tokio v1.0 or later is supported from casbin v2.0.6, we recommend that you upgrade the relevant components to ensure that they work properly. The last version that supports tokio v0.2 is casbin v2.0.5 , you can choose according to your needs.
- New a Casbin enforcer with a model file and a policy file:
use casbin::prelude::*;
#[tokio::main]
async fn main() -> Result<()> {
let mut e = Enforcer::new("examples/rbac_with_domains_model.conf", "examples/rbac_with_domains_policy.csv").await?;
e.enable_log(true);
e.enforce(("alice", "domain1", "data1", "read"))?;
Ok(())
}-
Add an enforcement hook into your code right before the access happens:
let sub = "alice"; // the user that wants to access a resource. let obj = "data1"; // the resource that is going to be accessed. let act = "read"; // the operation that the user performs on the resource. if let Ok(authorized) = e.enforce((sub, obj, act)) { if authorized { // permit alice to read data1 } else { // deny the request } } else { // error occurs }
💡 Please note that the Enforcer instance is not thread-safe, so in order to use it
in a environment where multiple threads might access it, you have to protect it
using an RwLock like so: let e = Arc::new(RwLock::new(e));.
- Supported models
- How it works?
- Features
- Documentation
- Online editor
- Tutorials
- Policy management
- Policy persistence
- Role manager
- Examples
- Middlewares
- Our adopters
- ACL (Access Control List)
- ACL with superuser
- ACL without users: especially useful for systems that don't have authentication or user log-ins.
- ACL without resources: some scenarios may target for a type of resources instead of an individual resource by using permissions like
write-article,read-log. It doesn't control the access to a specific article or log. - RBAC (Role-Based Access Control)
- RBAC with resource roles: both users and resources can have roles (or groups) at the same time.
- RBAC with domains/tenants: users can have different role sets for different domains/tenants.
- ABAC (Attribute-Based Access Control): syntax sugar like
resource.Ownercan be used to get the attribute for a resource. - RESTful: supports paths like
/res/*,/res/:idand HTTP methods likeGET,POST,PUT,DELETE. - Deny-override: both allow and deny authorizations are supported, deny overrides the allow.
- Priority: the policy rules can be prioritized like firewall rules.
In casbin-rs, an access control model is abstracted into a CONF file based on the PERM metamodel (Policy, Effect, Request, Matchers). So switching or upgrading the authorization mechanism for a project is just as simple as modifying a configuration. You can customize your own access control model by combining the available models. For example, you can get RBAC roles and ABAC attributes together inside one model and share one set of policy rules.
The most basic and simplest model in casbin-rs is ACL. ACL's model CONF is:
# Request definition
[request_definition]
r = sub, obj, act
# Policy definition
[policy_definition]
p = sub, obj, act
# Policy effect
[policy_effect]
e = some(where (p.eft == allow))
# Matchers
[matchers]
m = r.sub == p.sub && r.obj == p.obj && r.act == p.actAn example policy for ACL model is like:
p, alice, data1, read
p, bob, data2, write
It means:
- alice can read data1
- bob can write data2
What casbin-rs does:
- enforce the policy in the classic
{subject, object, action}form or a customized form as you defined, both allow and deny authorizations are supported. - handle the storage of the access control model and its policy.
- manage the role-user mappings and role-role mappings (aka role hierarchy in RBAC).
- support built-in superuser like
rootoradministrator. A superuser can do anything without explict permissions. - multiple built-in operators to support the rule matching. For example,
keyMatchcan map a resource key/foo/barto the pattern/foo*.
What casbin-rs does NOT do:
- authentication (aka verify
usernameandpasswordwhen a user logs in) - manage the list of users or roles. I believe it's more convenient for the project itself to manage these entities. Users usually have their passwords, and casbin-rs is not designed as a password container. However, casbin-rs stores the user-role mapping for the RBAC scenario.
https://casbin.org/docs/overview
You can also use the online editor (http://casbin.org/editor/) to write your casbin-rs model and policy in your web browser. It provides functionality such as syntax highlighting and code completion, just like an IDE for a programming language.
https://casbin.org/docs/tutorials
casbin-rs provides two sets of APIs to manage permissions:
- Management API: the primitive API that provides full support for casbin-rs policy management. See here for examples.
- RBAC API: a more friendly API for RBAC. This API is a subset of Management API. The RBAC users could use this API to simplify the code. See here for examples.
We also provide a web-based UI for model management and policy management:
- https://casbin.org/docs/adapters
- There also is example code on how to preload an existing policy into an adapter.
https://casbin.org/docs/role-managers
| Model | Model file | Policy file |
|---|---|---|
| ACL | basic_model.conf | basic_policy.csv |
| ACL with superuser | basic_model_with_root.conf | basic_policy.csv |
| ACL without users | basic_model_without_users.conf | basic_policy_without_users.csv |
| ACL without resources | basic_model_without_resources.conf | basic_policy_without_resources.csv |
| RBAC | rbac_model.conf | rbac_policy.csv |
| RBAC with resource roles | rbac_model_with_resource_roles.conf | rbac_policy_with_resource_roles.csv |
| RBAC with domains/tenants | rbac_model_with_domains.conf | rbac_policy_with_domains.csv |
| ABAC | abac_model.conf | N/A |
| RESTful | keymatch_model.conf | keymatch_policy.csv |
| Deny-override | rbac_model_with_deny.conf | rbac_policy_with_deny.csv |
| Priority | priority_model.conf | priority_policy.csv |
Authz middlewares for web frameworks: https://casbin.org/docs/middlewares
https://casbin.org/docs/adopters
This project exists thanks to all the people who contribute.
Thank you to all our backers! 🙏 [Become a backer]
Support this project by becoming a sponsor. Your logo will show up here with a link to your website. [Become a sponsor]
This project is licensed under the Apache 2.0 license.
If you have any issues or feature requests, please contact us. PR is welcomed.
- https://github.com/casbin/casbin-rs/issues
- Tencent QQ group: 546057381