Comments (27)
Thank you very much for this information.
Let's try a lucky blind fix from your dump...
Could you try the fix/bad_kaslr_ptr branch on your Q AVD ?
This should fix the issue on the Q x86 AVD (not the others). But if it works, I'll fix the other Android versions.
from aeroot.
Thank you for your feedback.
So, it will take a little more to fix Pie.
For Oreo, I pushed a new branch poc/selinux_validation.
Could you try it (without -append nokaslr).
The script will bypass the root credentials stage to try to set SElinux permissive.
So could you just check SELinux mode after executing aeroot.py daemon ?
from aeroot.
Thanks a lot.
Your welcome. And thank you too, your feedback allows to increase the compatibility of aeroot on different setups.
If you need any help to fix it for Android 9.0, please let me know how I can help.
Fixing Pie will need first a reverse engineering step from my part. I will keep you informed.
from aeroot.
Fine! Yep. I'll try to implement this workaround in aeroot soon.
Thank you!
from aeroot.
I am delighted that AEroot is now working properly on your setup.
Thank you for your comments, they really helped me.
from aeroot.
Hi!
In first place, are you sure you are running the Google Play tagged AVD ?
Typically this issue happens when you run the script with a not supported AVD.
from aeroot.
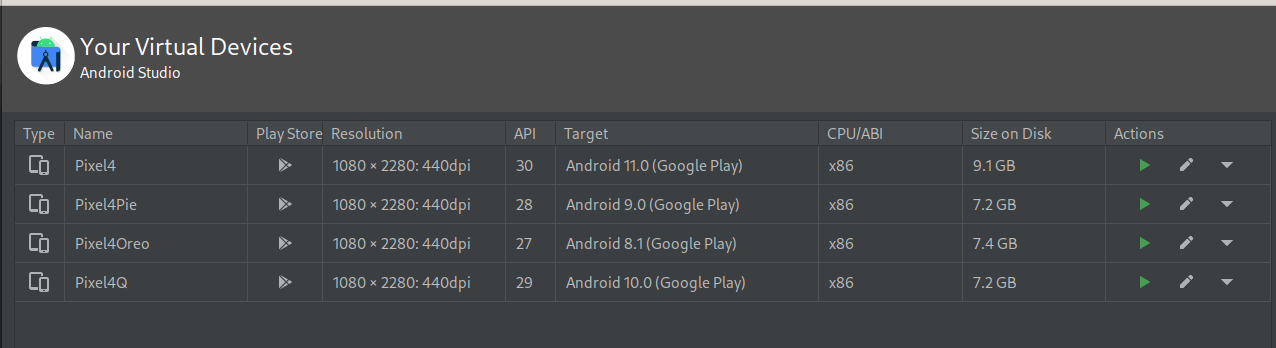
Hi!
Yes, I'm sure the images I've tested are those with Google Play Store. You can see them on the following screenshot:
from aeroot.
Hi!
Well, let's try to understand what's going on with your Android 10 AVD.
- What is your emulator version ? (
$ emulator -version) - Could you paste the content of the
ANDROID_SDK_PATH/system-images/android-29/google_apis_playstore/x86/build.propfile ?
from aeroot.
Emulator version:
./emulator -version
emulator: Android emulator version 30.5.3.0 (build_id 7196367) (CL:N/A)
Android emulator version 30.5.3.0 (build_id 7196367) (CL:N/A)
Copyright (C) 2006-2017 The Android Open Source Project and many others.
This program is a derivative of the QEMU CPU emulator (www.qemu.org).
build.prop contents:
┌─╼ arch [~/Android/Sdk/system-images/android-29/google_apis_playstore/x86]
└────╼ cat build.prop
# begin common build properties
# autogenerated by build/make/tools/buildinfo_common.sh
ro.system.build.date=Sat Sep 21 05:16:38 UTC 2019
ro.system.build.date.utc=1569042998
ro.system.build.fingerprint=google/sdk_gphone_x86/generic_x86:10/QSR1.190920.001/5891938:user/dev-keys
ro.system.build.id=QSR1.190920.001
ro.system.build.tags=dev-keys
ro.system.build.type=user
ro.system.build.version.incremental=5891938
ro.system.build.version.release=10
ro.system.build.version.sdk=29
ro.product.system.brand=google
ro.product.system.device=generic_x86
ro.product.system.manufacturer=Google
ro.product.system.model=Android SDK built for x86
ro.product.system.name=sdk_gphone_x86
# end common build properties
# begin build properties
# autogenerated by buildinfo.sh
ro.build.id=QSR1.190920.001
ro.build.display.id=QSR1.190920.001 dev-keys
ro.build.version.incremental=5891938
ro.build.version.sdk=29
ro.build.version.preview_sdk=0
ro.build.version.preview_sdk_fingerprint=REL
ro.build.version.codename=REL
ro.build.version.all_codenames=REL
ro.build.version.release=10
ro.build.version.security_patch=2019-09-05
ro.build.version.base_os=
ro.build.version.min_supported_target_sdk=23
ro.build.date=Sat Sep 21 05:16:38 UTC 2019
ro.build.date.utc=1569042998
ro.build.type=user
ro.build.user=android-build
ro.build.host=wpra9.hot.corp.google.com
ro.build.tags=dev-keys
ro.build.flavor=sdk_gphone_x86-user
ro.build.ab_update=false
# ro.product.cpu.abi and ro.product.cpu.abi2 are obsolete,
# use ro.product.cpu.abilist instead.
ro.product.cpu.abi=x86
ro.product.cpu.abilist=x86
ro.product.cpu.abilist32=x86
ro.product.cpu.abilist64=
ro.product.locale=en-US
ro.wifi.channels=
# ro.build.product is obsolete; use ro.product.device
ro.build.product=generic_x86
# Do not try to parse description or thumbprint
ro.build.description=sdk_gphone_x86-user 10 QSR1.190920.001 5891938 dev-keys
# end build properties
#
# from build/make/target/board/gsi_system_user.prop
#
# GSI always generate dex pre-opt in system image
ro.cp_system_other_odex=0
# GSI disables non-AOSP nnapi extensions on product partition
ro.nnapi.extensions.deny_on_product=true
# TODO(b/120679683): disable RescueParty before all problem apps solved
persist.sys.disable_rescue=true
# TODO(b/78105955): disable privapp_permissions checking before the bug solved
ro.control_privapp_permissions=disable
# TODO(b/136212765): the default for LMK
ro.lmk.kill_heaviest_task=true
ro.lmk.kill_timeout_ms=100
ro.lmk.use_minfree_levels=true
# end of build/make/target/board/gsi_system_user.prop
#
# ADDITIONAL_BUILD_PROPERTIES
#
ro.treble.enabled=true
net.bt.name=Android
from aeroot.
Thank you.
AVD seems to be the same here, and I can't reproduce the issue with your emulator version.
So I would need additional information.
First, a paranoid check of the AVD system image. In your ~/Android/Sdk/system-images/android-29/google_apis_playstore/x86 directory, could you paste the output of the following command:
sha1sum *.img kernel-ranchu-64Next, could you paste the content of those two files:
~/.android/avd/Pixel4Q.avd/hardware-qemu.ini
~/.android/avd/Pixel4Q.avd/config.ini
Then another paranoid check of your configuration. When your emulator is running your Pixel4Q AVD, could you paste me the output of the following command:
ps a | grep qemuAnd finally a little dump should be useful. When your emulator is running your Pixel4Q AVD, just run gdb, then:
set arch i386:x86-64:intel
target remote :1234
dump memory dump.bin 0xfffffe000002d000 0xfffffe0000038ff9
Could you send me the resulting dump.bin file.
Thank you in advance.
from aeroot.
Checksums:
┌─╼ arch [~/Android/Sdk/system-images/android-29/google_apis_playstore/x86]
└────╼ sha1sum *.img kernel-ranchu-64
3b71f43ff30f4b15b5cd85dd9e95ebc7e84eb5a3 encryptionkey.img
96282b5e66f10adc74547ca7441df290c3dad1ae ramdisk.img
738e7b606d9059840c863d4fee3f23037b5cd49e system.img
3b71f43ff30f4b15b5cd85dd9e95ebc7e84eb5a3 userdata.img
28fdb42d248fb194b7c9570afd6efc1e0f6014db vendor.img
e8865020796eac6f992d542cce09c52a7d73a025 kernel-ranchu-64
hardware-qemu.ini:
┌─╼ arch [~/.android/avd/Pixel4Q.avd]
└────╼ cat hardware-qemu.ini
hw.cpu.arch = x86
hw.cpu.model = qemu32
hw.cpu.ncore = 4
hw.ramSize = 2048
hw.screen = multi-touch
hw.mainKeys = false
hw.trackBall = false
hw.keyboard = true
hw.keyboard.lid = false
hw.keyboard.charmap = qwerty2
hw.dPad = false
hw.rotaryInput = false
hw.gsmModem = true
hw.gps = true
hw.battery = true
hw.accelerometer = true
hw.gyroscope = true
hw.audioInput = true
hw.audioOutput = true
hw.sdCard = true
hw.sdCard.path = /home/vinicius/.android/avd/Pixel4Q.avd/sdcard.img
disk.cachePartition = true
disk.cachePartition.path = /home/vinicius/.android/avd/Pixel4Q.avd/cache.img
disk.cachePartition.size = 66m
test.quitAfterBootTimeOut = -1
test.delayAdbTillBootComplete = 0
test.monitorAdb = 0
hw.lcd.width = 1080
hw.lcd.height = 2280
hw.lcd.depth = 16
hw.lcd.density = 440
hw.lcd.backlight = true
hw.lcd.vsync = 60
hw.gltransport = pipe
hw.gltransport.asg.writeBufferSize = 1048576
hw.gltransport.asg.writeStepSize = 4096
hw.gltransport.asg.dataRingSize = 32768
hw.gltransport.drawFlushInterval = 800
hw.displayRegion.0.1.xOffset = -1
hw.displayRegion.0.1.yOffset = -1
hw.displayRegion.0.1.width = 0
hw.displayRegion.0.1.height = 0
hw.displayRegion.0.2.xOffset = -1
hw.displayRegion.0.2.yOffset = -1
hw.displayRegion.0.2.width = 0
hw.displayRegion.0.2.height = 0
hw.displayRegion.0.3.xOffset = -1
hw.displayRegion.0.3.yOffset = -1
hw.displayRegion.0.3.width = 0
hw.displayRegion.0.3.height = 0
hw.display1.width = 0
hw.display1.height = 0
hw.display1.density = 0
hw.display1.xOffset = -1
hw.display1.yOffset = -1
hw.display1.flag = 0
hw.display2.width = 0
hw.display2.height = 0
hw.display2.density = 0
hw.display2.xOffset = -1
hw.display2.yOffset = -1
hw.display2.flag = 0
hw.display3.width = 0
hw.display3.height = 0
hw.display3.density = 0
hw.display3.xOffset = -1
hw.display3.yOffset = -1
hw.display3.flag = 0
hw.gpu.enabled = true
hw.gpu.mode = host
hw.initialOrientation = Portrait
hw.camera.back = virtualscene
hw.camera.front = emulated
vm.heapSize = 512
hw.sensors.light = true
hw.sensors.pressure = true
hw.sensors.humidity = true
hw.sensors.proximity = true
hw.sensors.magnetic_field = true
hw.sensors.magnetic_field_uncalibrated = true
hw.sensors.gyroscope_uncalibrated = true
hw.sensors.orientation = true
hw.sensors.temperature = true
hw.sensor.hinge = true
hw.sensor.hinge.count = 0
hw.sensor.hinge.type = 0
hw.sensor.hinge.sub_type = 0
hw.sensor.hinge.fold_to_displayRegion.0.1_at_posture = 1
hw.sensor.roll = false
hw.sensor.roll.count = 0
hw.sensor.roll.resize_to_displayRegion.0.1_at_posture = 6
hw.sensor.roll.resize_to_displayRegion.0.2_at_posture = 6
hw.sensor.roll.resize_to_displayRegion.0.3_at_posture = 6
hw.sensors.heart_rate = false
hw.useext4 = true
hw.arc = false
hw.arc.autologin = false
kernel.path = /home/vinicius/Android/Sdk/system-images/android-29/google_apis_playstore/x86//kernel-ranchu-64
kernel.newDeviceNaming = yes
kernel.supportsYaffs2 = no
disk.ramdisk.path = /home/vinicius/Android/Sdk/system-images/android-29/google_apis_playstore/x86//ramdisk.img
disk.systemPartition.initPath = /home/vinicius/Android/Sdk/system-images/android-29/google_apis_playstore/x86//system.img
disk.systemPartition.size = 2284m
disk.vendorPartition.initPath = /home/vinicius/Android/Sdk/system-images/android-29/google_apis_playstore/x86//vendor.img
disk.vendorPartition.size = 800m
disk.dataPartition.path = /home/vinicius/.android/avd/Pixel4Q.avd/userdata-qemu.img
disk.dataPartition.size = 6g
disk.encryptionKeyPartition.path = /home/vinicius/.android/avd/Pixel4Q.avd/encryptionkey.img
PlayStore.enabled = true
avd.name = Pixel4Q
avd.id = Pixel4Q
fastboot.forceColdBoot = false
android.sdk.root = /home/vinicius/Android/Sdk
android.avd.home = /home/vinicius/.android/avd
config.ini:
┌─╼ arch [~/.android/avd/Pixel4Q.avd]
└────╼ cat config.ini
AvdId = Pixel4Q
PlayStore.enabled = true
abi.type = x86
avd.ini.displayname = Pixel4Q
avd.ini.encoding = UTF-8
disk.dataPartition.size = 6442450944
fastboot.chosenSnapshotFile =
fastboot.forceChosenSnapshotBoot = no
fastboot.forceColdBoot = no
fastboot.forceFastBoot = yes
hw.accelerometer = yes
hw.arc = false
hw.audioInput = yes
hw.battery = yes
hw.camera.back = virtualscene
hw.camera.front = emulated
hw.cpu.arch = x86
hw.cpu.ncore = 4
hw.dPad = no
hw.device.hash2 = MD5:6b5943207fe196d842659d2e43022e20
hw.device.manufacturer = Google
hw.device.name = pixel_4
hw.gps = yes
hw.gpu.enabled = yes
hw.gpu.mode = auto
hw.initialOrientation = Portrait
hw.keyboard = yes
hw.lcd.density = 440
hw.lcd.height = 2280
hw.lcd.width = 1080
hw.mainKeys = no
hw.ramSize = 1536
hw.sdCard = yes
hw.sensors.orientation = yes
hw.sensors.proximity = yes
hw.trackBall = no
image.sysdir.1 = system-images/android-29/google_apis_playstore/x86/
runtime.network.latency = none
runtime.network.speed = full
sdcard.size = 512M
showDeviceFrame = yes
skin.dynamic = yes
skin.name = pixel_4
skin.path = /home/vinicius/Android/Sdk/skins/pixel_4
tag.display = Google Play
tag.id = google_apis_playstore
vm.heapSize = 256
QEMU running ps output:
┌─╼ arch [~/.android/avd/Pixel4Q.avd]
└────╼ ps aux | grep -i qemu
vinicius 7174 65.6 7.4 3831200 2289280 pts/0 Sl+ 11:27 2:47 /home/vinicius/Android/Sdk/emulator/qemu/linux-x86_64/qemu-system-x86_64 -avd Pixel4Q -no-snapstorage -qemu -s
vinicius 7500 0.0 0.0 6404 2416 pts/1 S+ 11:32 0:00 grep --colour=always -i qemu
Unfortunately I was unable to generate the dump file. You can see the GDB output below:
┌─╼ arch [~/.android/avd/Pixel4Q.avd]
└────╼ gdb -q
(gdb) set arch i386:x86-64:intel
The target architecture is set to "i386:x86-64:intel".
(gdb) target remote :1234
Remote debugging using :1234
warning: while parsing target description (at line 1): Could not load XML document "i386-64bit.xml"
warning: Could not load XML target description; ignoring
warning: No executable has been specified and target does not support
determining executable automatically. Try using the "file" command.
0xffffffffaaa8dfff in ?? ()
(gdb) dump memory dump.bin 0xfffffe000002d000 0xfffffe0000038ff9
Cannot access memory at address 0xfffffe0000038000
(gdb) i r
rax 0x0 0
rbx 0xffffffffab415480 -1421781888
rcx 0x9c732 640818
rdx 0x140000000000000 90071992547409920
rsi 0xffffffffab2b9e41 -1423204799
rdi 0xffffffffab28dd96 -1423385194
rbp 0xffffffffab403e30 0xffffffffab403e30
rsp 0xffffffffab403e08 0xffffffffab403e08
r8 0xffffb69540b87da1 -80722824495711
r9 0xffffb695411dbe80 -80722817859968
r10 0x0 0
r11 0xffff9c9d7fc1bc00 -109274709509120
r12 0x0 0
r13 0x0 0
r14 0xffffffffab403e67 -1421853081
r15 0x0 0
rip 0xffffffffaaa8dfff 0xffffffffaaa8dfff
eflags 0x200246 [ PF ZF IF ID ]
cs 0x10 16
ss 0x18 24
ds 0x0 0
es 0x0 0
fs 0x0 0
gs 0x0 0
(gdb)
from aeroot.
Here you can find a dump from 0xfffffe000002d000 to 0xfffffe0000038000, got by running dump memory dump.bin 0xfffffe000002d000 0xfffffe0000038000
https://drive.google.com/file/d/1yrmZMQkzkGDoumcpwth7TdcciGbiNkgB/view?usp=sharing
from aeroot.
The fix worked like a charm. Thank you.
from aeroot.
Nice!
Do you get the same kind of error on your 8.1 and 9.0 AVD ? Because for these versions, the way to get the address of the init descriptor is a bit different.
May be an output like the first one you've posted could be helpful on 8.1 and 9.0 AVD.
Thank you in advance.
Edit: I push a new fix on fix/bad_kaslr_ptr because the SELinux disabling feature was broken. Could you confirm that SELinux status is Permissive in a rooted shell on your AVD Q ?
from aeroot.
In fact the first fix made SELinux stay on "Enforcing" policy and I didn't notice yesterday. But the latest commit fixed this too and now SELinux policy is "Permissive". Now everything seems fine for Android 10.
I get the same kind of error for Android 8.1 and 9.0. I've modified the script to add some debug messages.
Android 9.0 output:
┌─╼ arch [~/Tools/AERoot]
└────╼ ./aeroot.py daemon
AERoot (Android Emulator ROOTing system) v. 0.2
_ _ _ _
__|_|___ ( \ ( ) ( )
( _____/ \ \ _| |_| |
| (|_|__ _____\ \ (_ _ _)
(_____ ) (_____)) ) _| (_) |
/\_|_|) | / / (_ _ _)
\_______) / / | | | |
|_| (_/ (_) (_)
[+] Detected: Android 9.0 (Pie) x86
[+] Search for [adbd] process in memory (this may take a while) ...
get_task_structs function, before while, current_prev_ptr: 0xffff88004d4d86a0
read_addr(0xffff88004d4d86a0) - gdb "x/a 0xffff88004d4d86a0" response:
[
{
"type": "log",
"message": null,
"payload": "x/a 0xffff88004d4d86a0\\n",
"stream": "stdout"
},
{
"type": "console",
"message": null,
"payload": "0xffff88004d4d86a0:\\t0x0\\n",
"stream": "stdout"
},
{
"type": "result",
"message": "done",
"payload": null,
"token": null,
"stream": "stdout"
}
]
get_task_structs function, before while, current_task_struct: 0x-698
get_task_structs, while iter 1, current_prev_ptr: 0x8
read_addr(0x8) - gdb "x/a 0x8" response:
[
{
"type": "log",
"message": null,
"payload": "x/a 0x8\\n",
"stream": "stdout"
},
{
"type": "console",
"message": null,
"payload": "0x8:\\t",
"stream": "stdout"
},
{
"type": "log",
"message": null,
"payload": "Cannot access memory at address 0x8\\n",
"stream": "stdout"
},
{
"type": "result",
"message": "error",
"payload": {
"msg": "Cannot access memory at address 0x8"
},
"token": null,
"stream": "stdout"
}
]
[+] Exiting.
Traceback (most recent call last):
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 451, in <module>
process_addr = find_task_struct(gdb_helper, avd_conf, target_process)
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 224, in find_task_struct
return next(filter(lambda x: process.match(gdb, avd, x), get_task_structs(gdb, avd)), None)
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 250, in get_task_structs
current_task_struct = gdb.read_addr(current_prev_ptr) - avd.get("offset_to_tasks")
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 136, in read_addr
return int(response.split("\\t")[1].replace("\\n", ""), 16)
ValueError: invalid literal for int() with base 16: ''
Android 9.0 checksums:
┌─╼ arch [~/Android/Sdk/system-images/android-28/google_apis_playstore/x86]
└────╼ sha1sum *.img kernel-ranchu-64
3b71f43ff30f4b15b5cd85dd9e95ebc7e84eb5a3 encryptionkey.img
44281b6d4a6c9907463f503fb4fc3b2bc940c35c ramdisk.img
c1ffdd940aaa7327e00c6ce9960370163e5dbced system.img
3b71f43ff30f4b15b5cd85dd9e95ebc7e84eb5a3 userdata.img
8dad9fd1026d94f18a8ec0b6207dfcaccecf41db vendor.img
bfe33955742e4e17ab819dbfcf21a944f85175d1 kernel-ranchu-64
Android 8.1 output:
┌─╼ arch [~/Tools/AERoot]
└╼ ./aeroot.py daemon
AERoot (Android Emulator ROOTing system) v. 0.2
_ _ _ _
__|_|___ ( \ ( ) ( )
( _____/ \ \ _| |_| |
| (|_|__ _____\ \ (_ _ _)
(_____ ) (_____)) ) _| (_) |
/\_|_|) | / / (_ _ _)
\_______) / / | | | |
|_| (_/ (_) (_)
[+] Detected: Android 8.1 (Oreo) x86
[+] Search for [adbd] process in memory (this may take a while) ...
get_task_structs function, before while, current_prev_ptr: 0xe1cb02cc
read_addr(0xe1cb02cc) - gdb "x/a 0xe1cb02cc" response:
[
{
"type": "log",
"message": null,
"payload": "x/a 0xe1cb02cc\\n",
"stream": "stdout"
},
{
"type": "console",
"message": null,
"payload": "0xe1cb02cc:\\t0xffffffff\\n",
"stream": "stdout"
},
{
"type": "result",
"message": "done",
"payload": null,
"token": null,
"stream": "stdout"
}
]
get_task_structs function, before while, current_task_struct: 0xfffffd37
get_task_structs, while iter 1, current_prev_ptr: 0x100000003
read_addr(0x100000003) - gdb "x/a 0x100000003" response:
[
{
"type": "log",
"message": null,
"payload": "x/a 0x100000003\\n",
"stream": "stdout"
},
{
"type": "console",
"message": null,
"payload": "0x3:\\t",
"stream": "stdout"
},
{
"type": "log",
"message": null,
"payload": "Cannot access memory at address 0x3\\n",
"stream": "stdout"
},
{
"type": "result",
"message": "error",
"payload": {
"msg": "Cannot access memory at address 0x3"
},
"token": null,
"stream": "stdout"
}
]
[+] Exiting.
Traceback (most recent call last):
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 451, in <module>
process_addr = find_task_struct(gdb_helper, avd_conf, target_process)
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 224, in find_task_struct
return next(filter(lambda x: process.match(gdb, avd, x), get_task_structs(gdb, avd)), None)
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 250, in get_task_structs
current_task_struct = gdb.read_addr(current_prev_ptr) - avd.get("offset_to_tasks")
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 136, in read_addr
return int(response.split("\\t")[1].replace("\\n", ""), 16)
ValueError: invalid literal for int() with base 16: ''
Android 8.1 checksums:
┌─╼ arch [~/Android/Sdk/system-images/android-27/google_apis_playstore/x86]
└╼ sha1sum *.img kernel-ranchu
3b71f43ff30f4b15b5cd85dd9e95ebc7e84eb5a3 encryptionkey.img
5b9d24451218096900379d5c84c308cbf5e02c8a ramdisk.img
cc36431e5884e55fd714ac70e1cc23f1bcd0f7b7 system.img
a891b2676493ca9b64146a62aef88fdbc08b03eb userdata.img
12e14d15d6b6999d26880bc4010ee9fd9edd1d75 vendor.img
d7e9e62515c889ce8c5ce3c0bb48ec4e89e8d188 kernel-ranchu
If you need any dump file, please let me know.
from aeroot.
Thank you for these outputs.
Well, I tried a lazy fix for Pie x86 in c172699.
For Oreo, could you try to launch your emulator as following before using aeroot:
emulator @Pixel4Oreo -no-snapshot-load -qemu -s -append nokaslr
from aeroot.
Hi. The fix for Pie x86 didn't work. Below you can see the output:
┌─╼ arch [~/Tools/AERoot]
└────╼ ./aeroot.py daemon
AERoot (Android Emulator ROOTing system) v. 0.2
_ _ _ _
__|_|___ ( \ ( ) ( )
( _____/ \ \ _| |_| |
| (|_|__ _____\ \ (_ _ _)
(_____ ) (_____)) ) _| (_) |
/\_|_|) | / / (_ _ _)
\_______) / / | | | |
|_| (_/ (_) (_)
[+] Detected: Android 9.0 (Pie) x86
[+] Search for [adbd] process in memory (this may take a while) ...
read_addr(0xffff88004d4c8b20) - gdb "x/a 0xffff88004d4c8b20" response:
[
{
"type": "log",
"message": null,
"payload": "x/a 0xffff88004d4c8b20\\n",
"stream": "stdout"
},
{
"type": "console",
"message": null,
"payload": "0xffff88004d4c8b20:\\t0x0\\n",
"stream": "stdout"
},
{
"type": "result",
"message": "done",
"payload": null,
"token": null,
"stream": "stdout"
}
]
mem_init_ptr: 0xbc584c
read_addr(0xbc584c) - gdb "x/a 0xbc584c" response:
[
{
"type": "log",
"message": null,
"payload": "x/a 0xbc584c\\n",
"stream": "stdout"
},
{
"type": "console",
"message": null,
"payload": "0xbc584c:\\t",
"stream": "stdout"
},
{
"type": "log",
"message": null,
"payload": "Cannot access memory at address 0xbc584c\\n",
"stream": "stdout"
},
{
"type": "result",
"message": "error",
"payload": {
"msg": "Cannot access memory at address 0xbc584c"
},
"token": null,
"stream": "stdout"
}
]
[+] Exiting.
Traceback (most recent call last):
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 451, in <module>
process_addr = find_task_struct(gdb_helper, avd_conf, target_process)
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 224, in find_task_struct
return next(filter(lambda x: process.match(gdb, avd, x), get_task_structs(gdb, avd)), None)
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 229, in get_task_structs
find_init(gdb, avd)
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 219, in find_init
avd["init_addr"] = gdb.read_addr(mem_init_ptr) - avd.get("offset_to_tasks")
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 136, in read_addr
return int(response.split("\\t")[1].replace("\\n", ""), 16)
ValueError: invalid literal for int() with base 16: ''
For Android 8, after running the emulator with ./emulator -avd Pixel4Oreo -no-snapshot-load -qemu -s -append noaslr, the AERoot still doesn't work. You can see the output below:
┌─╼ arch [~/Tools/AERoot]
└╼ ./aeroot.py daemon
AERoot (Android Emulator ROOTing system) v. 0.2
_ _ _ _
__|_|___ ( \ ( ) ( )
( _____/ \ \ _| |_| |
| (|_|__ _____\ \ (_ _ _)
(_____ ) (_____)) ) _| (_) |
/\_|_|) | / / (_ _ _)
\_______) / / | | | |
|_| (_/ (_) (_)
[+] Detected: Android 8.1 (Oreo) x86
[+] Search for [adbd] process in memory (this may take a while) ...
get_task_structs function, before while, current_prev_ptr: 0xe1cb02cc
read_addr(0xe1cb02cc) - gdb "x/a 0xe1cb02cc" response:
[
{
"type": "log",
"message": null,
"payload": "x/a 0xe1cb02cc\\n",
"stream": "stdout"
},
{
"type": "console",
"message": null,
"payload": "0xe1cb02cc:\\t0xffffffff\\n",
"stream": "stdout"
},
{
"type": "result",
"message": "done",
"payload": null,
"token": null,
"stream": "stdout"
}
]
get_task_structs function, before while, current_task_struct: 0xfffffd37
get_task_structs, while iter 1, current_prev_ptr: 0x100000003
read_addr(0x100000003) - gdb "x/a 0x100000003" response:
[
{
"type": "log",
"message": null,
"payload": "x/a 0x100000003\\n",
"stream": "stdout"
},
{
"type": "console",
"message": null,
"payload": "0x3:\\t",
"stream": "stdout"
},
{
"type": "log",
"message": null,
"payload": "Cannot access memory at address 0x3\\n",
"stream": "stdout"
},
{
"type": "result",
"message": "error",
"payload": {
"msg": "Cannot access memory at address 0x3"
},
"token": null,
"stream": "stdout"
}
]
[+] Exiting.
Traceback (most recent call last):
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 451, in <module>
process_addr = find_task_struct(gdb_helper, avd_conf, target_process)
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 224, in find_task_struct
return next(filter(lambda x: process.match(gdb, avd, x), get_task_structs(gdb, avd)), None)
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 250, in get_task_structs
current_task_struct = gdb.read_addr(current_prev_ptr) - avd.get("offset_to_tasks")
File "/home/vinicius/Tools/AERoot/./aeroot.py", line 136, in read_addr
return int(response.split("\\t")[1].replace("\\n", ""), 16)
ValueError: invalid literal for int() with base 16: ''
from aeroot.
It worked for Oreo.
After running ./emulator -avd Pixel4Oreo -no-snapshot-load -qemu -s and running aeroot.py daemon on selinux_validation branch, SELinux policy was changed to permissive, as can be seen below:
┌─╼ arch [~/Tools/AERoot]
└╼ ./aeroot.py daemon
AERoot (Android Emulator ROOTing system) v. 0.2
_ _ _ _
__|_|___ ( \ ( ) ( )
( _____/ \ \ _| |_| |
| (|_|__ _____\ \ (_ _ _)
(_____ ) (_____)) ) _| (_) |
/\_|_|) | / / (_ _ _)
\_______) / / | | | |
|_| (_/ (_) (_)
[+] Detected: Android 8.1 (Oreo) x86
[+] Switching SELinux to permissive...
[+] Exiting.
┌─╼ arch [~/Tools/AERoot]
└────╼ adb shell
generic_x86:/ $ getenforce
Permissive
generic_x86:/ $
from aeroot.
Ok.
Is 66b8b4e fixing Oreo ?
from aeroot.
Yes. It fixed properly as can be seen below:
┌─╼ arch [~/Tools/AERoot]
└────╼ git checkout remotes/origin/fix/bad_kaslr_ptr
Previous HEAD position was 67371c0 script modification to validate selinux
HEAD is now at 66b8b4e fix the way to get init descriptor on Android 8.1 x86
┌─╼ arch [~/Tools/AERoot]
└────╼ git log
┌─╼ arch [~/Tools/AERoot]
└────╼ ./aeroot.py daemon
AERoot (Android Emulator ROOTing system) v. 0.2
_ _ _ _
__|_|___ ( \ ( ) ( )
( _____/ \ \ _| |_| |
| (|_|__ _____\ \ (_ _ _)
(_____ ) (_____)) ) _| (_) |
/\_|_|) | / / (_ _ _)
\_______) / / | | | |
|_| (_/ (_) (_)
[+] Detected: Android 8.1 (Oreo) x86
[+] Search for [adbd] process in memory (this may take a while) ...
[+] [adbd] process found. Overwriting credentials.
[+] Switching SELinux to permissive...
[+] Exiting.
┌─╼ arch [~/Tools/AERoot]
└────╼ adb shell
generic_x86:/ # id
uid=0(root) gid=0(root) groups=0(root),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats),3009(readproc),3011(uhid) context=u:r:shell:s0
generic_x86:/ # getenforce
Permissive
generic_x86:/ #
Thanks a lot.
If you need any help to fix it for Android 9.0, please let me know how I can help.
from aeroot.
I think a mem dump from your Pie AVD could help me:
dump memory dump.bin 0xffff88004d400000 0xffff88004d4fffff
from aeroot.
You can find the dump file here:
https://drive.google.com/file/d/1aNBMPF1HH61n4jdmhoc4YzEX3mpJvAor/view?usp=sharing
Emulator command:
./emulator -avd Pixel4Pie -no-snapshot-load -qemu -s
GDB log:
┌─╼ arch [~/Tools/AERoot]
└╼ gdb -q
(gdb) set arch i386:x86-64:intel
The target architecture is set to "i386:x86-64:intel".
(gdb) target remote :1234
Remote debugging using :1234
warning: while parsing target description (at line 1): Could not load XML document "i386-64bit.xml"
warning: Could not load XML target description; ignoring
warning: No executable has been specified and target does not support
determining executable automatically. Try using the "file" command.
0xffffffffba833944 in ?? ()
(gdb) dump memory dump.bin 0xffff88004d400000 0xffff88004d4fffff
(gdb) quit
from aeroot.
Thank you.
from aeroot.
I'm trying to find a workaround for Pie.
I pushed the branch poc/pie-find-kernel-base.
Could you try to execute kernel_base.py with your Pie AVD running ?
If it works it should give you something like this:
kernel base: 0xffffffffb5000000
swapper comm field: swapper/0
selinux mode: 0x1
Thank you in advance.
from aeroot.
Hi. I've tried running kernel_base.py. Here is the output:
┌─╼ arch [~/Tools/AERoot]
└╼ ./kernel_base.py
search for kernel base...
kernel base: 0xffffffffaae00000
swapper comm field: swapper/0
selinux mode: 0x1
I hope it means your workaround worked.
from aeroot.
Here come the fix. 0f667ac
from aeroot.
It worked. Thank you so much.
You can see below AERoot output on on bad_kaslr_ptr branch:
┌─╼ arch [~/Tools/AERoot]
└────╼ ./aeroot.py daemon
AERoot (Android Emulator ROOTing system) v. 0.2
_ _ _ _
__|_|___ ( \ ( ) ( )
( _____/ \ \ _| |_| |
| (|_|__ _____\ \ (_ _ _)
(_____ ) (_____)) ) _| (_) |
/\_|_|) | / / (_ _ _)
\_______) / / | | | |
|_| (_/ (_) (_)
[+] Detected: Android 9.0 (Pie) x86
[+] Search for [adbd] process in memory (this may take a while)...
[+] [adbd] process found. Overwriting credentials.
[+] Switching SELinux to permissive...
[+] Exiting.
┌─╼ arch [~/Tools/AERoot]
└────╼ adb shell
generic_x86_arm:/ # id
uid=0(root) gid=0(root) groups=0(root),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats),3009(readproc),3011(uhid) context=u:r:shell:s0
generic_x86_arm:/ # getenforce
Permissive
generic_x86_arm:/ #
from aeroot.
Related Issues (11)
- pygdbmi-0.10.0.0 is not compatible HOT 2
- [exp][feature] AERoot GDB Python support check
- [exp][feature] Kernel config integrity check
- [macOS] Kernel memory mapping failure at cold boot HOT 1
- Fix error handling on not supported kernel
- Emulator console auth token cannot be read with dockerized version HOT 2
- Always getting "Android version not supported. Aborting." in MAC HOT 12
- [feature] Add Android 14 support
- None value not handled in avd
- [feature] Add v6 kernel support
Recommend Projects
-
 React
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
 Typescript
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
-
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.

from aeroot.